Application security is one of those topics everyone agrees is important, right up until the budget discussion starts. Then things get vague. Some teams spend heavily on tools and still ship vulnerable code. Others do almost nothing and hope for the best. Most fall somewhere in between, unsure whether they are underinvesting or wasting money.
The problem is not that application security is unpredictable. It is that its costs are often misunderstood. Security is treated as a line item instead of an ongoing discipline tied to how software is actually built. This article breaks down what application security really costs, where the money usually goes, and what tends to deliver real value versus expensive noise.
No scare stories. No vendor pricing tables. Just a grounded look at what teams should expect when they decide to take application security seriously.
How Much Application Security Typically Costs
In practice, application security cost is a mix of external services and internal effort. For most teams, it is not a single large expense, but a set of ongoing investments spread across development, testing, and validation. On average, companies spend $10,000 to $50,000+ per year on external application security services, alongside dedicated engineering time for prevention and fixes.
Typical cost ranges look like this:
- הערכת פגיעות: about $3,000 to $10,000 per engagement.
- Penetration testing for key applications: usually $15,000 to $30,000, with complex systems reaching $50,000+.
- Structured security audits or ASVS-based reviews: roughly $10,000 to $25,000, depending on scope.
- Internal effort: commonly around 10 percent of engineering time allocated to security-related work.
The real difference between low and high security spend is rarely price alone. It comes down to when and how security is applied. Teams that invest earlier and more consistently tend to stay closer to the lower end of these ranges over time.
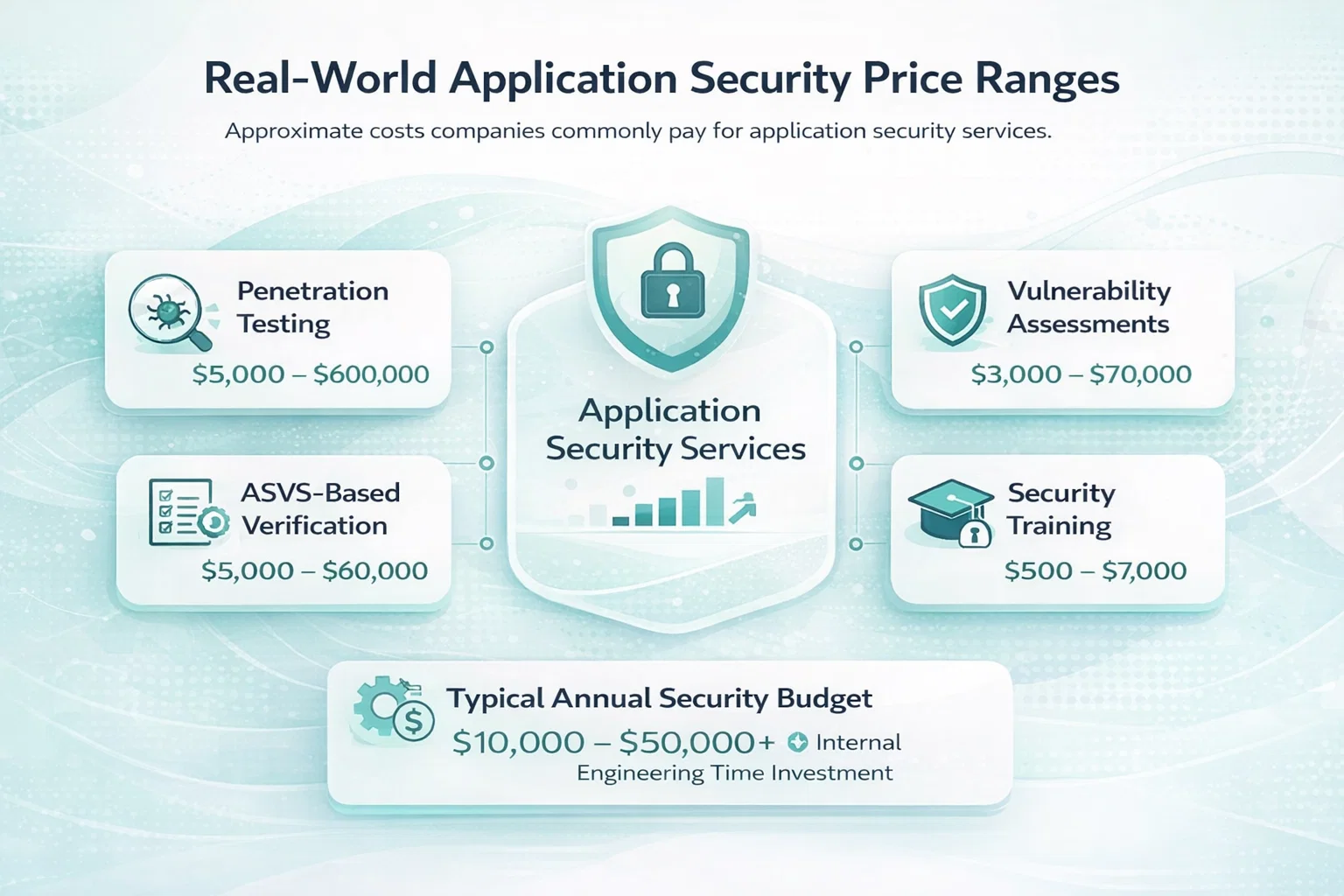
Real-World Application Security Price Ranges
Talking about application security cost without real numbers is not very helpful. Teams need rough benchmarks to plan budgets, set expectations, and explain decisions internally. While no two environments are the same, there are clear price patterns across the industry.
The ranges below reflect what companies are commonly paying today for application security services. Think of them as planning numbers, not fixed quotes.
Penetration Testing Costs
Penetration testing is often the most visible security expense. It involves skilled testers actively trying to break into your application in ways real attackers would.
Typical Penetration Test Pricing
- Small or basic web application: usually $5,000 to $15,000
- Mid-sized web application with authentication and APIs: roughly $15,000 to $30,000
- Mobile application testing (iOS or Android): commonly $12,000 to $35,000
- Complex enterprise applications or cloud environments: often $30,000 to $60,000 or more
These engagements typically include manual testing, reporting, and a debrief. Prices rise when applications have complex business logic, many integrations, or strict compliance expectations.
What Drives Penetration Testing Cost Up
Several factors consistently affect pricing:
- Number of applications, APIs, or services in scope
- Whether testing requires authenticated access and role-based scenarios
- Depth of testing expected beyond surface-level issues
- Frequency of testing per year
For many teams, penetration testing is performed once or twice a year for critical systems rather than continuously.
Vulnerability Assessment and Security Audit Costs
Vulnerability assessments and security audits take a broader view than penetration testing. They focus on identifying weaknesses, misconfigurations, and systemic issues rather than simulating full attacks.
Common Price Ranges
- Basic vulnerability assessment: typically $3,000 to $10,000
- Application-focused security audit: often $10,000 to $30,000
- Large or multi-application audit: can reach $40,000 to $70,000+
These services are often used as entry points for organizations starting to formalize their security posture. They are also common ahead of compliance reviews or customer security assessments.
ASVS-Based Application Security Verification
Some organizations prefer structured verification against defined security requirements instead of generic audits. OWASP ASVS-based reviews fall into this category.
Typical ASVS Verification Costs
- Small application with limited scope: around $5,000 to $10,000
- Medium-sized production application: roughly $10,000 to $25,000
- Large enterprise system: commonly $25,000 to $60,000+
ASVS-based reviews tend to be more systematic and less noisy than broad scans. They are especially useful for teams that want clarity on which security controls exist and which do not.
Security Training and Awareness Costs
Training is one of the least expensive and highest-impact security investments, yet it is often underfunded.
Typical Training Investment
- Basic secure development training per engineer: usually $500 to $2,000
- Advanced security or penetration testing training: often $3,000 to $7,000 per person
In many organizations, the larger cost is not the course itself but the time engineers spend learning. That time investment often pays for itself quickly through fewer recurring vulnerabilities.
Internal Application Security Effort
Not all application security cost shows up on invoices. A large portion comes from internal time allocation.
For many teams, a realistic baseline looks like this:
- Around 10 percent of engineering time dedicated to security-related work
- This includes threat modeling, secure design discussions, fixing issues, and maintaining tests
This is not lost productivity. It is preventive effort that reduces rework, incidents, and release stress later.
What a Realistic Annual Security Budget Looks Like
When you combine external services and internal effort, most organizations end up with a blended approach.
For a typical product team, that often means:
- $10,000 to $50,000+ per year on external security services
- Plus ongoing internal time investment across development and QA
Highly regulated industries, large platforms, or organizations with frequent releases often exceed these numbers. Smaller teams with focused scope and good security habits may stay below them.
Why These Numbers Vary So Much
Wide price ranges are not a sign of chaos. They reflect real differences in risk, complexity, and maturity.
Teams with clear architecture, strong internal practices, and realistic expectations tend to spend less over time. Teams that rely on last-minute audits and heavy tooling often spend more without improving security outcomes.
A-listware: A Long-Term Partner for Secure Software Delivery
ב A-listware, we approach application security as part of everyday engineering, not a separate layer added at the end. With more than 25 years of experience working with enterprises, growing businesses, and startups, we’ve learned that security works best when it is built into how teams design, develop, and test software from the start.
We form dedicated development teams that integrate directly into our clients’ workflows and processes. Acting as an extension of in-house teams, we apply secure coding practices, testing standards, and quality controls as part of normal delivery. This reduces late-stage rework, avoids unnecessary friction, and helps teams move faster without compromising reliability.
Our focus is on consistency and clarity. We support our teams with strong communication, local leadership, and access to experienced engineers across a wide range of technologies. By aligning development, testing, and infrastructure work early, we help clients build software that scales smoothly and stays secure as their products and organizations grow.
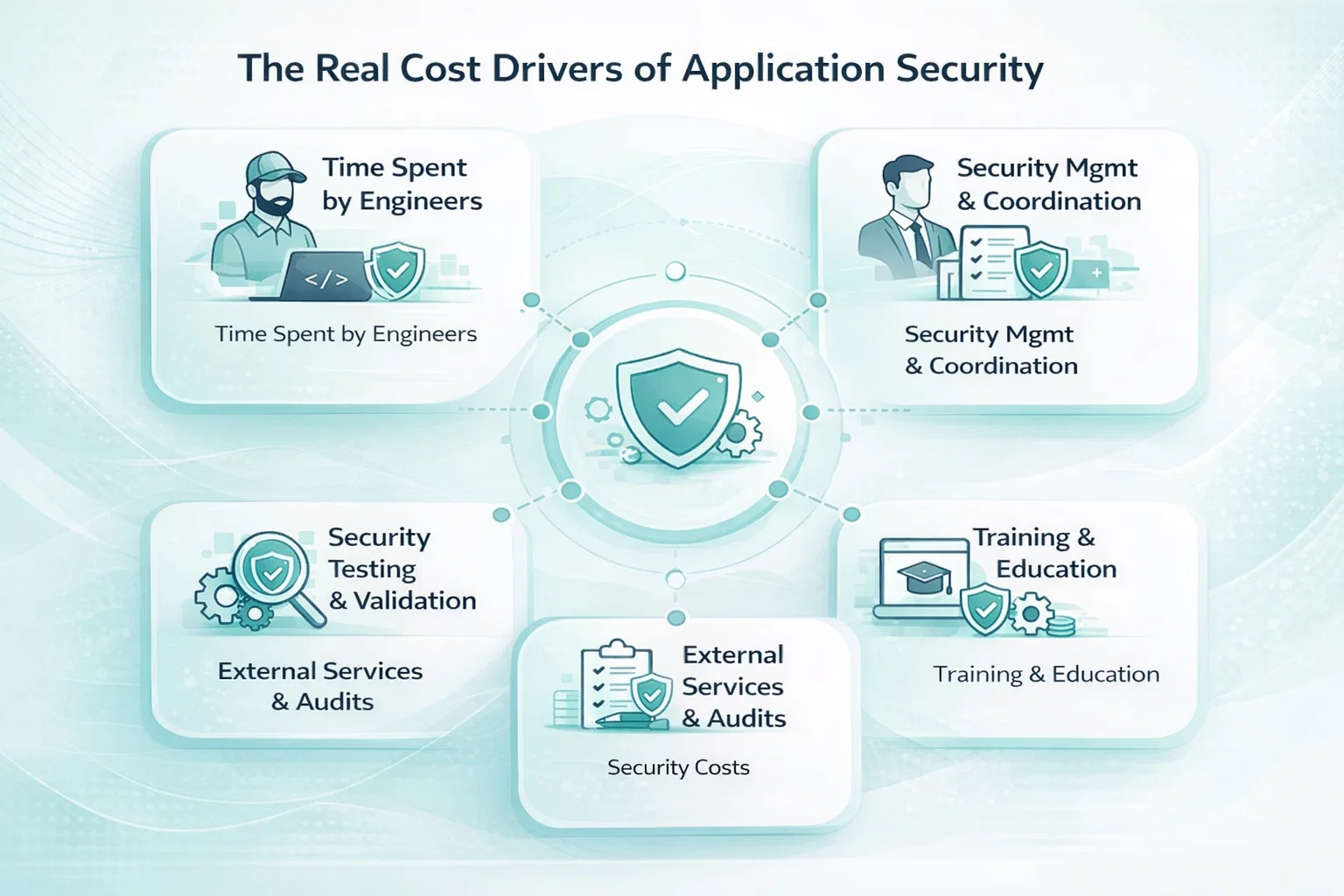
The Real Cost Drivers of Application Security
To understand application security cost, it helps to stop thinking in terms of products and start thinking in terms of effort. Most security spending falls into five categories.
Time Spent by Engineers
This is the largest and most overlooked cost. Engineers spend time learning secure coding practices, participating in threat modeling sessions, fixing vulnerabilities, and reviewing security requirements. None of this shows up as a security invoice, but it is real cost.
A common rule of thumb in mature organizations is to allocate around 10 percent of engineering time to security-related activities. This includes learning, prevention, and testing. That number is not fixed, but it reflects a realistic balance between delivery speed and risk control.
Security Management and Coordination
Someone needs to own the application security program. That does not always mean a full-time security team, especially in smaller companies. But it does mean dedicated time for planning, prioritization, and coordination.
This role includes maintaining standards, tracking progress, aligning with frameworks, and acting as a bridge between development, QA, and leadership. Without this function, security work becomes fragmented and inefficient.
Training and Education
Security training is one of the highest return investments a team can make. Teaching developers how vulnerabilities happen and how to avoid them prevents entire classes of issues before they appear in code.
The cost here is mostly time, not money. Structured training sessions, onboarding modules, and occasional deep dives into specific topics deliver long-term benefits that tools cannot replicate.
Security Testing and Validation
This includes manual testing, penetration testing, and structured verification against security standards. Whether done internally or with external support, testing costs scale with application complexity and release frequency.
The key cost factor is focus. Testing that targets real risk and meaningful scenarios is far more cost-effective than broad, shallow scans that generate long reports and little insight.
External Services and Audits
External audits, compliance assessments, and third-party penetration tests are often necessary, especially for regulated industries. These costs are easier to quantify but should be viewed as supplements, not substitutes, for internal security capability.
When external services replace internal understanding, costs rise and learning stalls.
Why Early Security Costs Less Than Late Security
One of the most consistent findings across industries is that the cost of fixing security issues increases dramatically the later they are found.
A design flaw caught during architecture discussions might cost an hour of whiteboard time. The same flaw discovered during testing could require weeks of refactoring. Found after release, it might trigger emergency patches, customer notifications, and long-term trust damage.
This is why practices like threat modeling and secure design reviews have such high return. They shift cost forward, when changes are cheap and flexible.
Organizations that invest early often spend less overall, even if their upfront security effort looks higher on paper.
The Hidden Cost of False Positives and Noise
When Security Tools Create More Work Than Value
Another major cost driver in application security is wasted effort. Automated tools can generate thousands of findings, many of which are irrelevant or low risk. Without proper triage, teams end up investigating issues that have little real impact while genuinely dangerous problems wait in the backlog.
How Noise Erodes Trust and Focus
This situation creates two kinds of waste. Developers lose time and patience as they chase alerts that lead nowhere. Security teams lose credibility when everything is marked as urgent. Over time, real issues are ignored because nothing stands out as truly important.
Why Reducing Noise Lowers Security Cost
Reducing noise is one of the most effective ways to control application security cost. In practice, that usually means running fewer tools, configuring them more carefully, and improving collaboration between security and development. When teams agree on what actually matters, security work becomes faster, calmer, and far more effective.
When Outsourcing Application Security Makes Financial Sense
Not every organization can or should build deep application security expertise internally. For many teams, especially scale-ups and mid-sized companies, selective outsourcing is a practical choice.
External specialists can provide focused testing, validation, and expertise that internal teams lack. They can also help tune tools, validate findings, and provide risk context.
The key is integration. Outsourced security works best when it supports internal teams rather than replacing them. When external reports are dropped over the wall without discussion, costs rise and value drops.
From a cost perspective, targeted external support often reduces overall spending by avoiding overstaffing and accelerating learning.
Why Application Security Cost Keeps Rising in 2026 and Beyond
Application security costs are rising because software development itself is moving faster. Continuous releases, frequent updates, and short delivery cycles leave less room for manual checks. The faster code reaches production, the more effort is required to ensure security keeps up without slowing teams down.
At the same time, applications are becoming more interconnected. Modern systems rely on open-source libraries, third-party APIs, and external services that expand the attack surface. Even well-built code can inherit risk from dependencies that teams do not fully control or actively maintain.
New pressures continue to build. AI-generated code introduces unfamiliar patterns that require additional review, and regulatory expectations around software accountability are increasing. None of this makes security impossible, but it does make informal approaches expensive. Teams that invest early in structured security programs tend to adapt more easily, while those relying on last-minute fixes usually pay more over time.
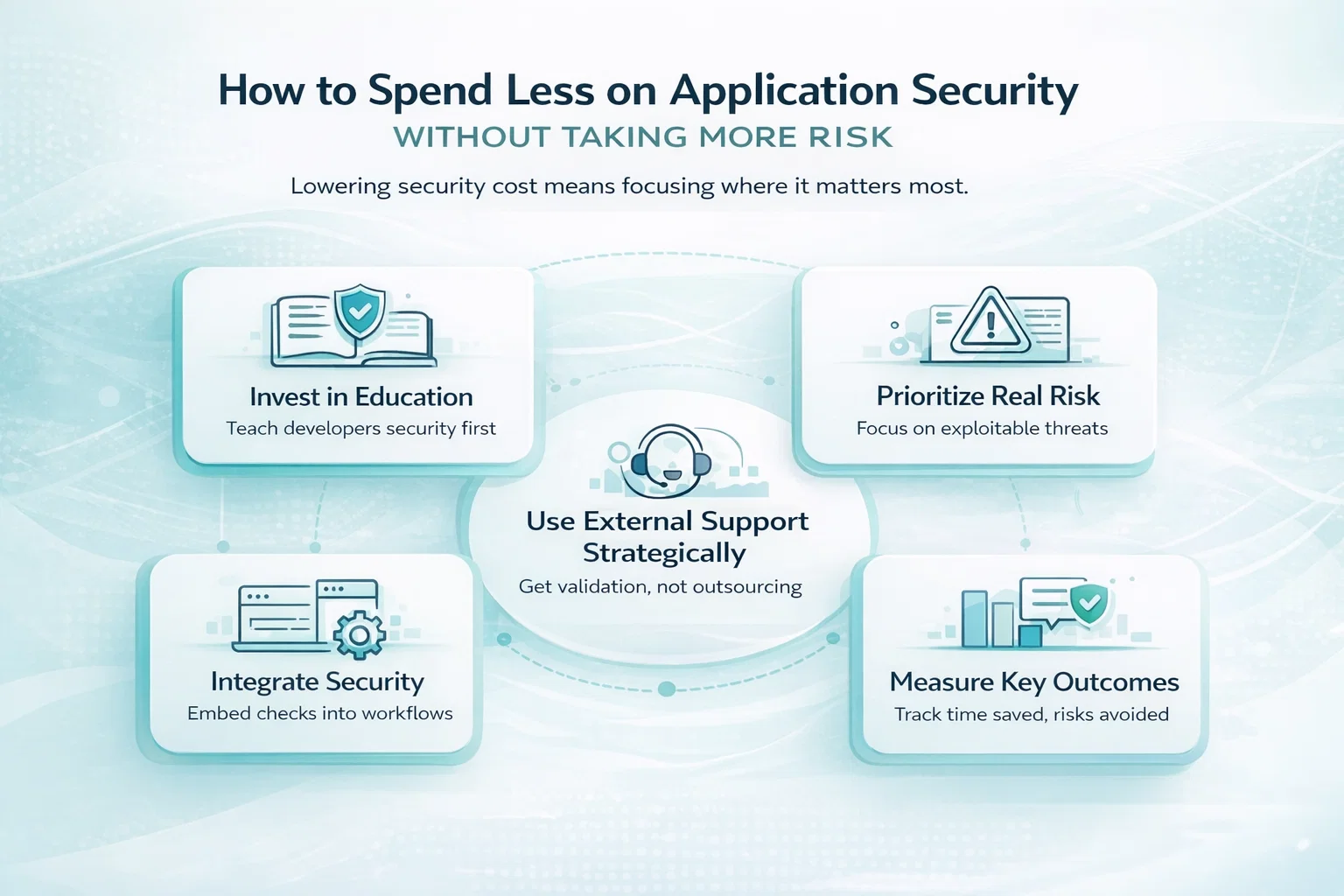
How to Spend Less on Application Security Without Taking More Risk
Lowering application security cost does not mean cutting corners. It means being intentional about where time and money actually make a difference.
- Invest in education before tools. Teach developers how vulnerabilities happen and how to avoid them. A team that understands security writes safer code long before scanners get involved.
- Prioritize real risk over issue volume. Not every finding deserves the same attention. Focus first on vulnerabilities that can realistically be exploited and cause real damage.
- Integrate security into existing workflows. Build security checks into design reviews, development, and testing instead of adding separate processes that slow everyone down.
- Measure effort and outcomes, not just findings. Track how much time is spent preventing issues and how many high-risk problems are avoided, not just how many alerts are generated.
- Use external support strategically. Bring in specialists for validation, deep testing, or knowledge gaps, but avoid outsourcing responsibility for understanding your own risk.
When security becomes part of how teams think and work, costs stabilize. Fewer issues reach production, fewer emergencies happen, and security stops feeling like a constant surprise.
Conclusion: The Real Question Is Not Cost, but Control
Application security cost is often framed as a necessary evil or an unpredictable expense. In reality, it is a reflection of how an organization builds software.
Teams that treat security as an afterthought pay more, both financially and operationally. Teams that treat it as a shared responsibility spend more intentionally and get more value.
The real question is not how much application security costs, but whether that cost is planned or accidental. Planned security investment builds resilience, confidence, and trust. Accidental security spending shows up as breaches, delays, and damage control.
In the long run, application security is not a cost center. It is a form of operational discipline. And like most disciplines, it is cheaper to practice than to ignore.
שאלות נפוצות
- How much does application security really cost for a typical company?
There is no single number, but most companies spend a mix of internal time and external services. For many product teams, external security services range from $10,000 to $50,000+ per year, depending on scope and risk. On top of that, teams usually dedicate around 10 percent of engineering time to security-related work such as training, threat modeling, and fixing issues early.
- Why does application security feel expensive even when budgets are modest?
Because the cost is often hidden. Much of application security happens inside normal development work, not as a separate line item. When security is handled late or poorly, the cost shows up as delays, rework, stress, or incidents. That makes security feel expensive even when the actual spend is not high.
- Is application security mostly about buying tools?
No. Tools can help, but they are not the foundation. The biggest cost drivers are people, time, and process. Teams that invest in training, clear ownership, and early security practices often spend less on tools and get better results.
- How often should application security testing be done?
It depends on how often your software changes and how critical it is. Many teams run penetration tests once or twice a year for key systems, combined with ongoing internal testing and reviews. Applications that change frequently or handle sensitive data may need more regular validation.
- Can small teams afford proper application security?
Yes. Smaller teams often benefit the most from early security habits because they can build them in before complexity grows. Basic training, lightweight threat modeling, and focused testing are usually enough to reduce most common risks without large budgets.


