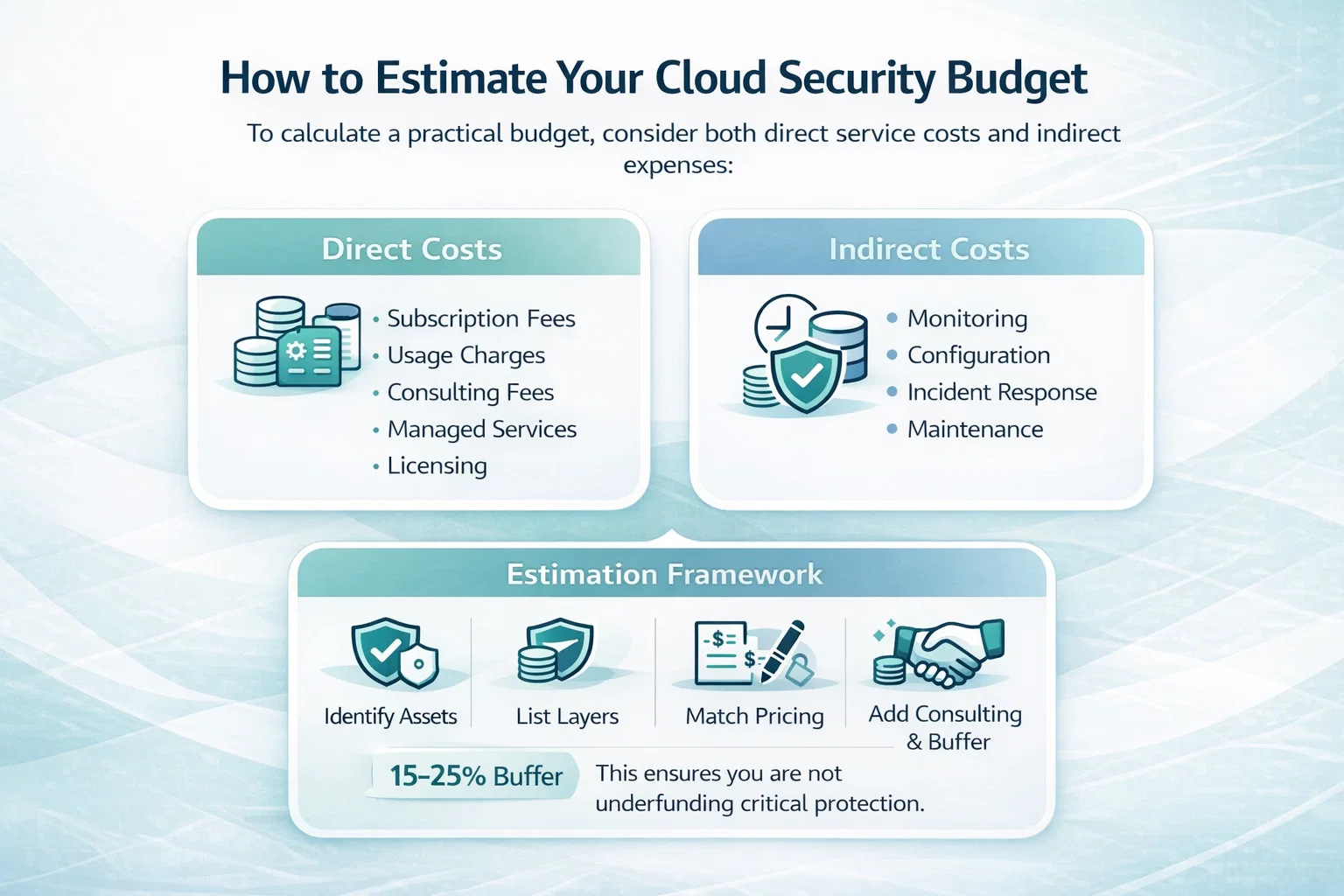
Data loss prevention (DLP) tools aren’t just for big corporations anymore. Small and mid-sized businesses are starting to take data protection seriously too, because one mistake can get expensive fast. But figuring out what DLP really costs isn’t always straightforward. The pricing depends on who’s using it, how much data you’re trying to protect, and how deep you want the protection to go.
Some companies spend only a few thousand dollars per year on DLP, while others invest tens of thousands depending on their scale and customization needs. In this article, we’ll walk through what drives those numbers up (or down), what kind of price ranges you’re likely to see, and how to get real value without drowning in unnecessary features.
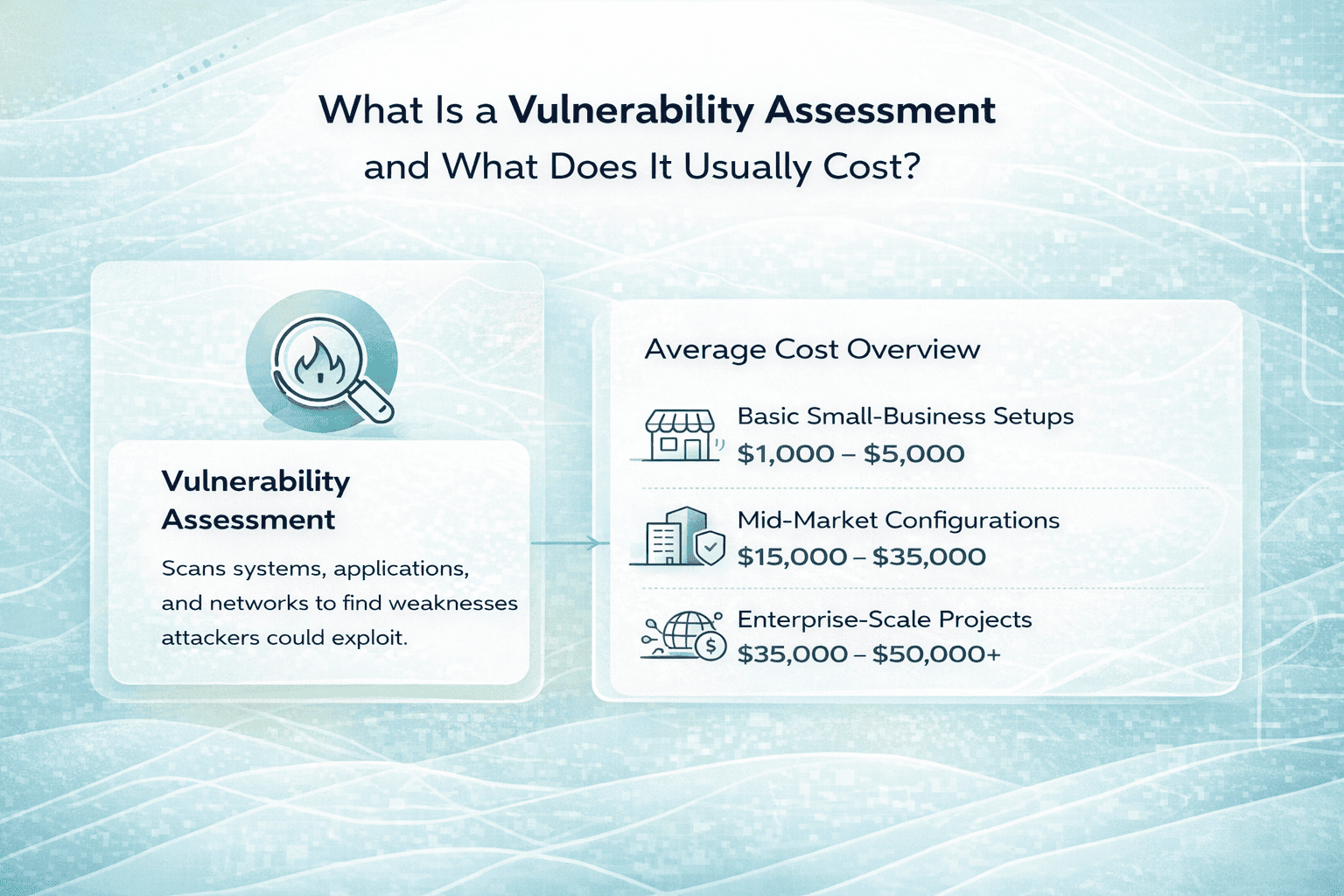
What Is Data Loss Prevention and How Much Does It Cost on Average?
Data loss prevention, or DLP, is a mix of tools and strategies that help businesses stop sensitive information from being lost, leaked, or mishandled. It’s not just about blocking cyberattacks. DLP also prevents accidental data sharing, internal misuse, and violations of privacy laws.
Think of it as a safety net for things like customer records, health data, financial information, or proprietary files. Whether it’s an employee sending the wrong email attachment or someone trying to move company data to a personal device, DLP is built to catch those actions before damage is done.
As for cost, DLP can range from around $10 to $90 per user, depending on how many people you’re protecting, how much data you’re handling, and what features you actually need. For small and mid-sized businesses, it’s possible to start with basic protection and scale up as needs grow.

Why DLP Pricing Isn’t One-Size-Fits-All
Before diving into numbers, it helps to know what shapes the price in the first place. DLP isn’t a single product. It’s a category made up of tools, services, and policies that protect sensitive data from being lost, leaked, or stolen.
Some companies need full coverage across endpoints, networks, cloud services, and email. Others might just want to block employees from accidentally sharing credit card data over Slack. The size of your team, how much data you’re handling, and what compliance rules you’re trying to meet all play a role.
Think of DLP costs like building a house. The price depends on the square footage, the materials, the number of people using it, and whether you’re hiring a contractor or doing it yourself.
How We Help Businesses Manage DLP Cost-Effectively
За адресою Програмне забезпечення списку А, we work with companies that are serious about protecting their data but need to do it in a way that actually fits their budget. Whether you’re rolling out a full data loss prevention strategy or simply adding DLP as part of a broader security upgrade, we help you avoid over-engineering the solution or overspending on features that don’t serve your core goals.
What makes DLP costs spike isn’t just the software itself. It’s also the integration work, the custom rule sets, the time spent tuning alerts, and the follow-up support when something goes wrong. That’s why we approach DLP as part of a bigger picture. We build development and consulting teams that understand how your systems work together, and we make sure everything runs smoothly across infrastructure, applications, and user access points.
With over two decades of experience in software development and IT consulting, we’ve seen how easily data security plans fall apart when the architecture behind them is fragmented. Our teams are built to reduce that friction. We keep your operations lean, assign dedicated experts who understand the context, and work closely with your team so you don’t waste time or money on tools that don’t fit.
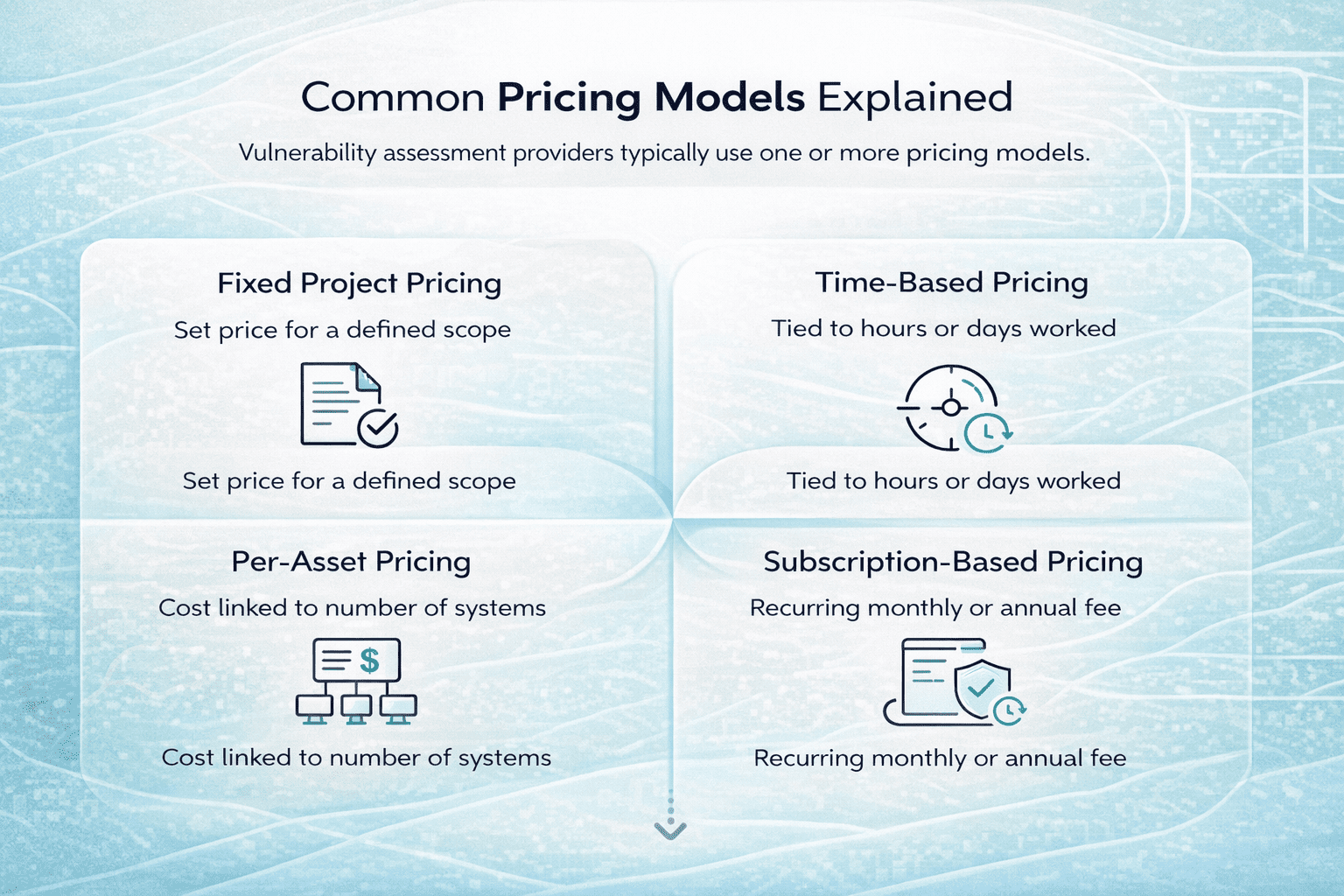
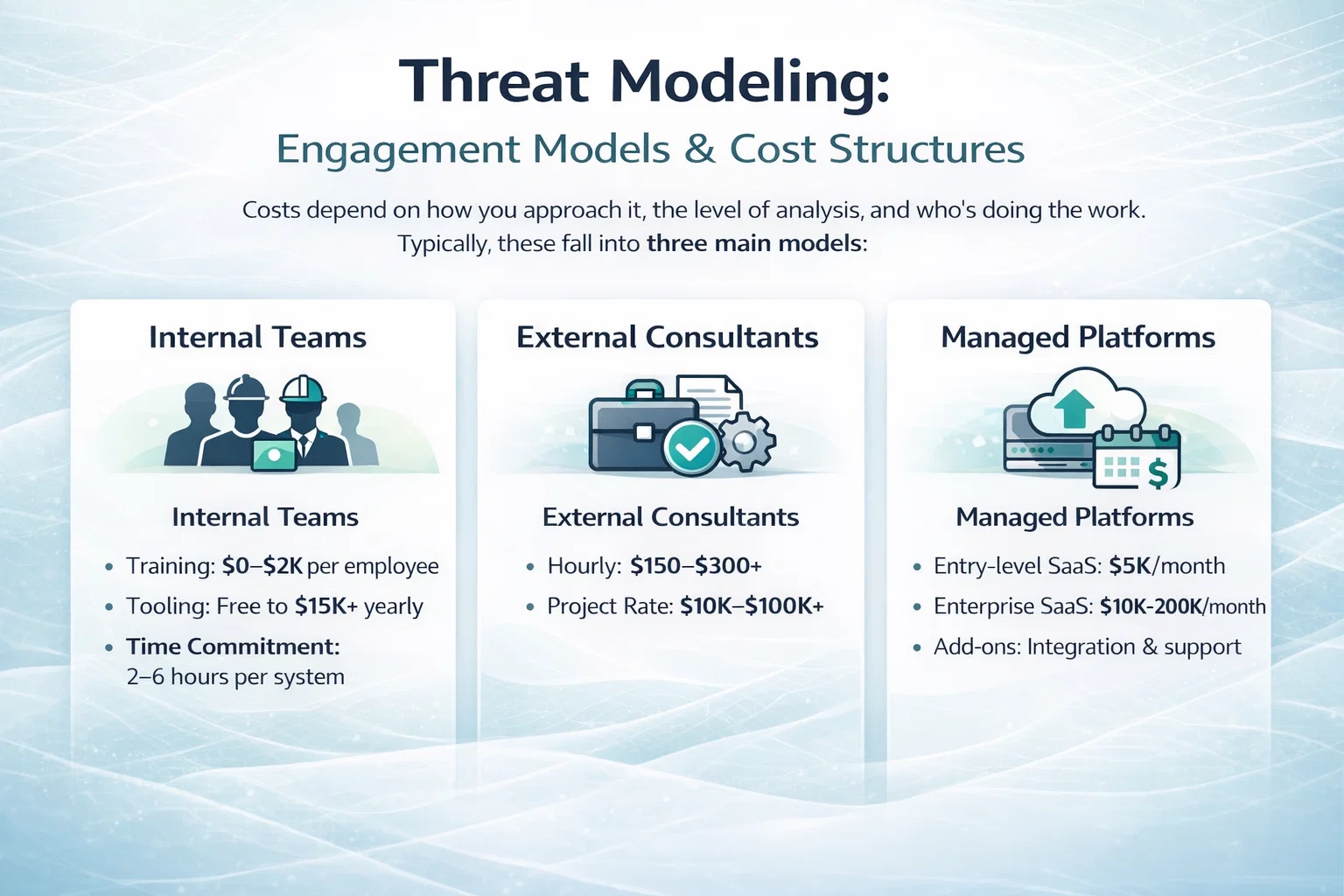
The Main Ways DLP Is Priced
Most DLP tools and platforms fall into one of three pricing models. Some vendors blend them, but the structure usually starts here:
1. Per-User Pricing
This is the most common approach, especially for cloud-based DLP systems. You pay a monthly or annual fee for each user or endpoint that’s being monitored.
- Typical range: $10 to $90 per user per year.
- Good for: Companies with consistent headcounts and clear roles.
- Watch out for: Unexpected charges if contractors or temp staff get added suddenly.
2. Per Data Volume
Instead of charging by the user, some vendors price their tools based on how much data is being scanned, protected, or stored.
- Typical range: $1,000 to $4,000 per terabyte.
- Good for: Data-heavy environments like healthcare, finance, or analytics teams.
- Watch out for: Costs scaling fast if data isn’t cleaned or archived regularly.
3. Per Feature or Module
This model lets you pick specific DLP features like endpoint protection, email filtering, or cloud monitoring. You pay separately for each.
- Typical range: $30 to $150 per module (the price can vary significantly).
- Good for: Gradual rollouts or when only a few functions are needed.
- Watch out for: Feature creep and a la carte pricing stacking up quickly.
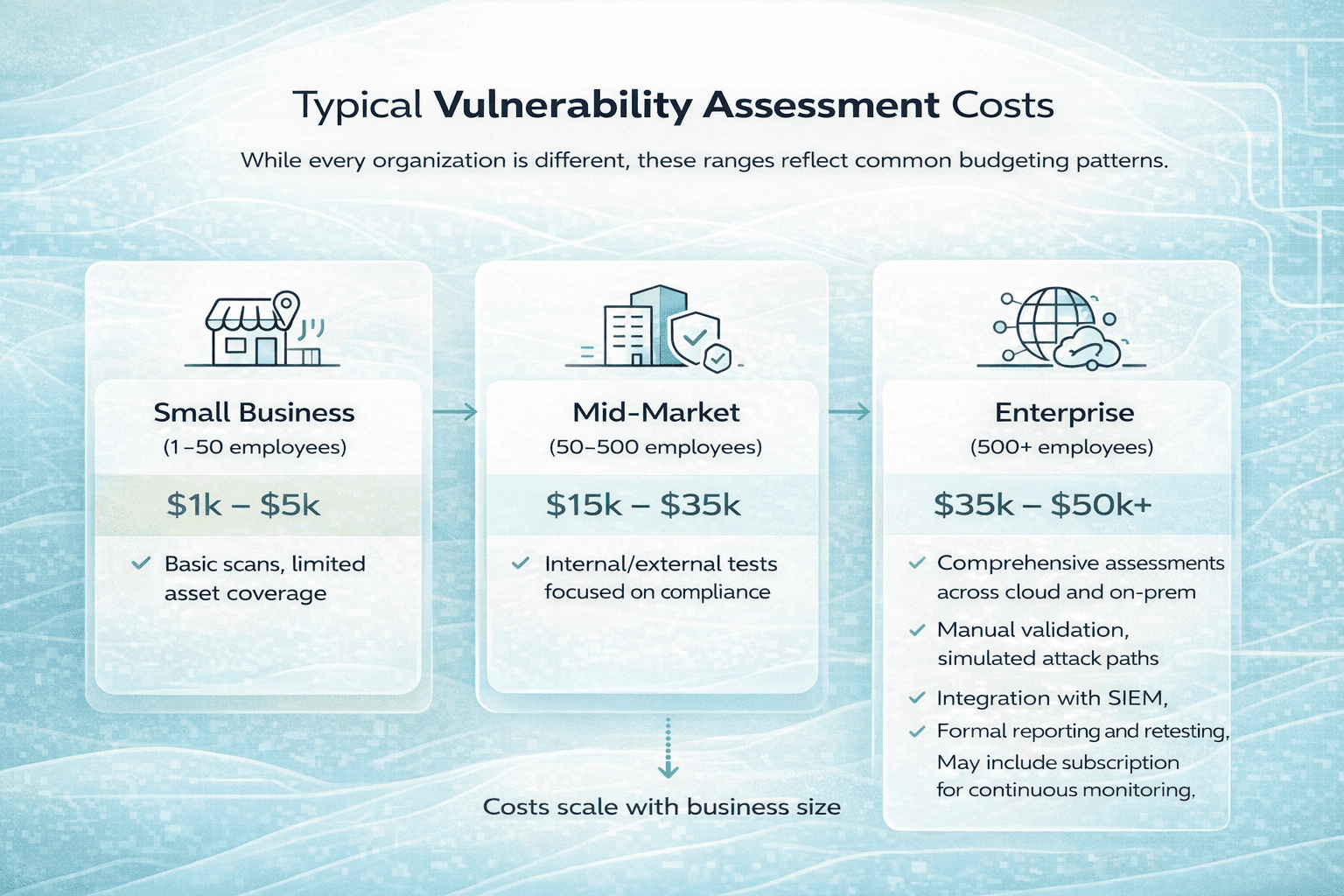
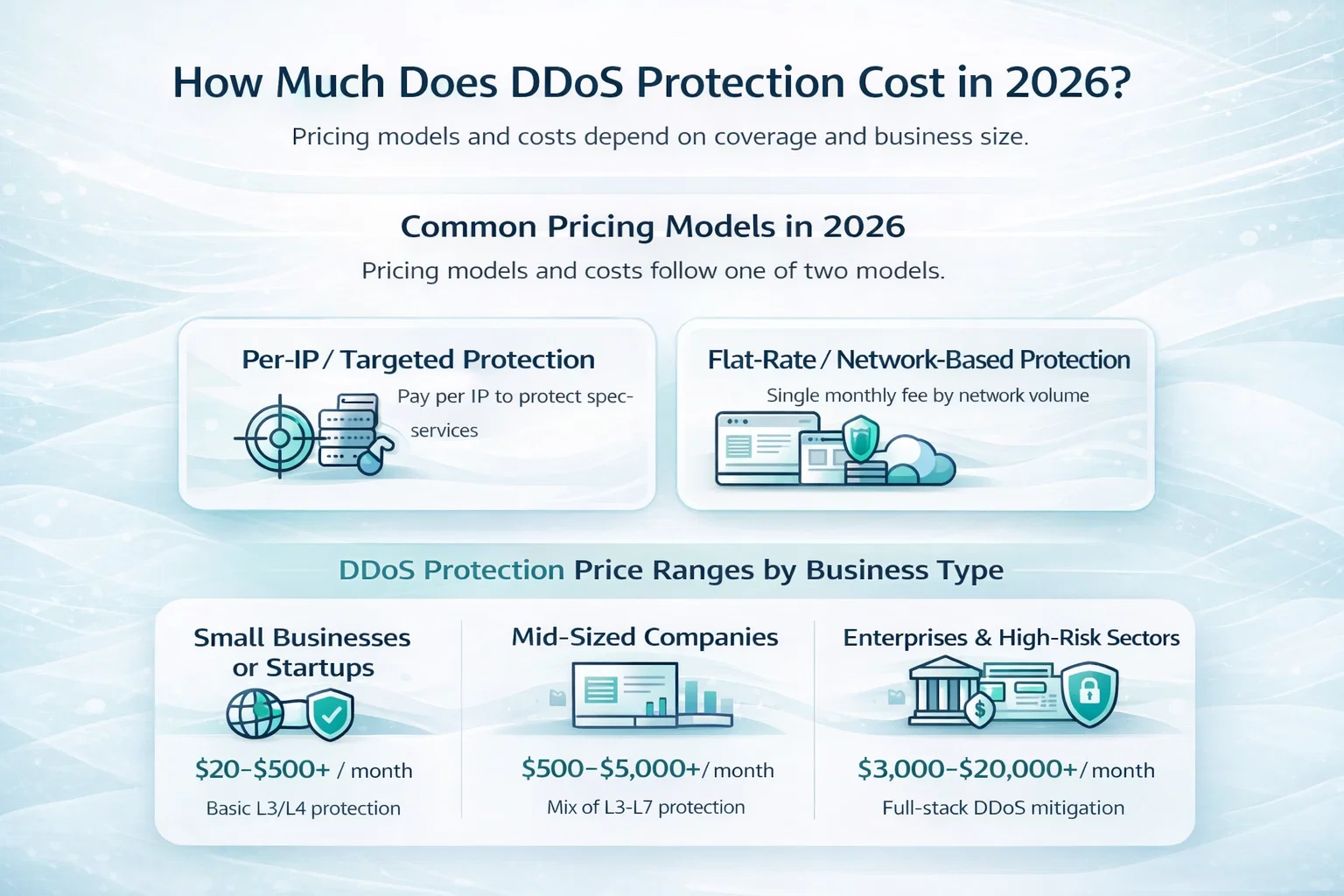
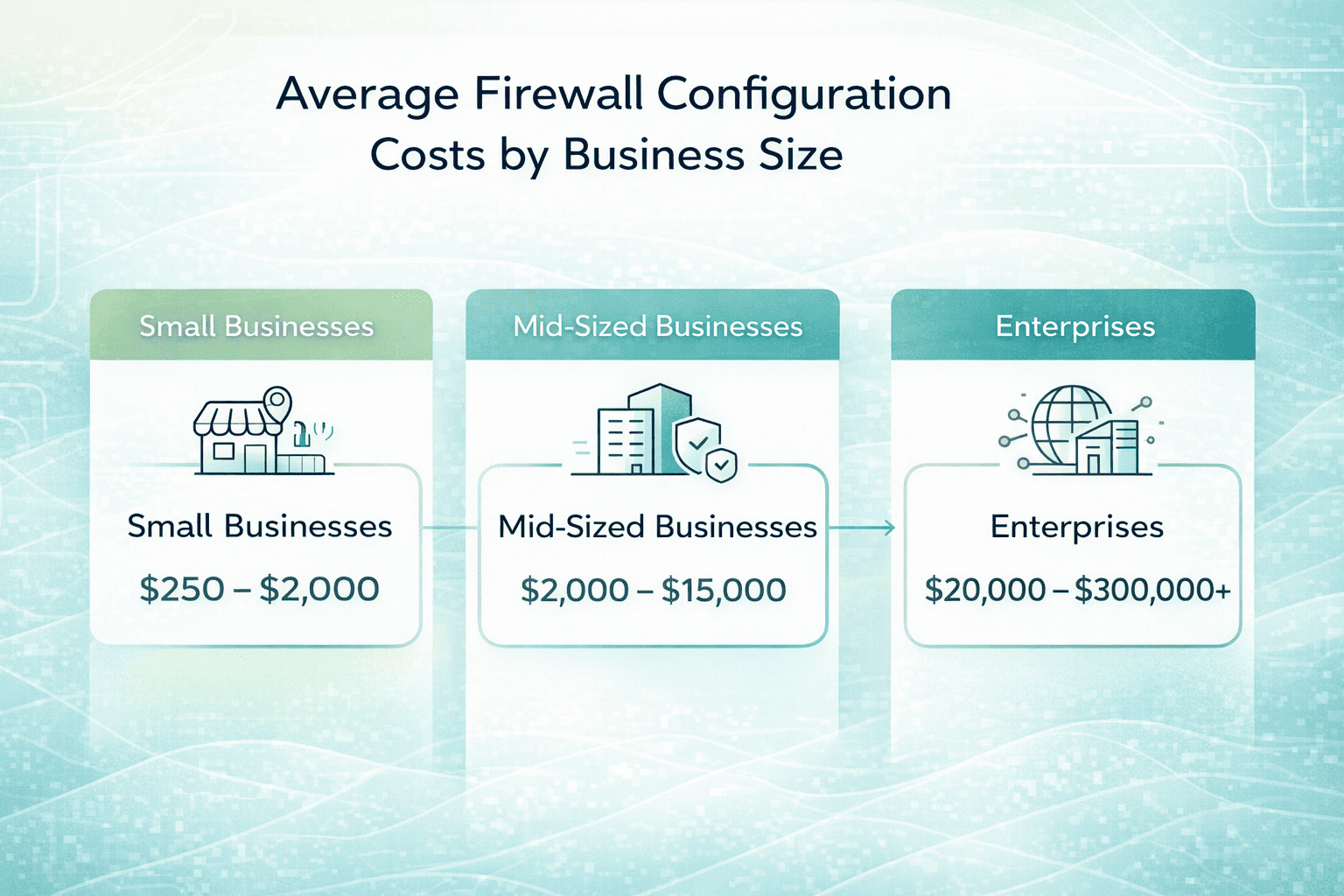
Estimated Average DLP Costs (By Company Type)
| Company Size | Typical Annual Cost (USD) | Cost Drivers |
| Small Business (10-50 users) | $6,000 – $36,000 | Per-user pricing, basic modules |
| Midsize Company (50-250 users) | $30,000 – $180,000 | Add-ons like cloud and endpoint DLP |
| Enterprise (250+ users) | $180,000 – $1,200,000+ | Full coverage, customization, pro services |
Note that these are ballpark estimates based on multiple vendor models and industry analysis. Actual costs can shift significantly depending on data sensitivity, architecture, and compliance.
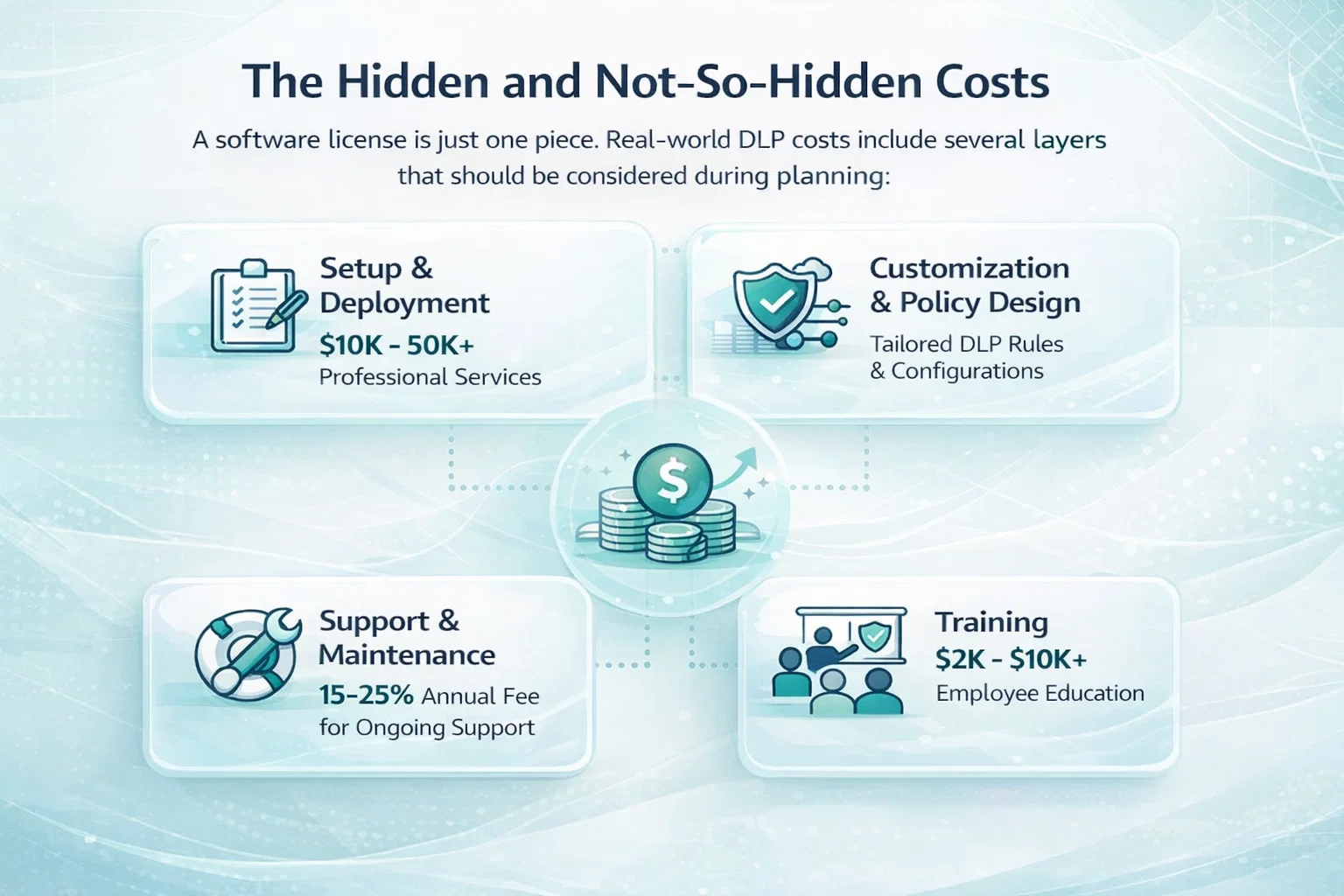
The Hidden and Not-So-Hidden Costs
The software license is just one piece. Real-world DLP costs include several layers that should be considered during planning:
Setup and Deployment
Getting a DLP solution up and running involves more than flipping a switch. There’s implementation work, system configuration, and integration with the tools your team already uses. For larger organizations or more complex environments, setup costs can stretch well into the five-figure range.
It’s not unusual to see professional services come in anywhere between $10,000 and $50,000, especially when there are multiple systems to secure. Cloud-based platforms might ease some of that initial lift, but they come with their own challenges, like routing sensitive data properly through the right channels.
Customization and Policy Design
Every business handles data differently, so cookie-cutter settings rarely cut it. Creating DLP rules that actually fit your workflows takes time. Whether you’re classifying files by content type, limiting access by user role, or adding specific triggers for email and endpoint behavior, tailoring those controls adds layers of complexity. Some companies try to handle this internally, while others bring in outside consultants to make sure everything aligns with compliance needs and operational habits.
Підтримка та обслуговування
Once DLP is deployed, it’s not a set-it-and-forget-it situation. Like any other system that’s supposed to adapt to your data and behavior patterns, it needs regular updates and monitoring. That includes patches, upgrades, bug fixes, and policy tuning. Most providers charge an ongoing support fee that runs around 15% to 25% of the software’s license cost each year. The better the support, the faster you can recover when something misfires or a policy needs adjusting on the fly.
Training
No DLP system works well without people who know how to use it. Training your staff isn’t just about getting the IT team up to speed – it also includes educating employees on how and why policies are enforced. This reduces alert fatigue, lowers the odds of false positives, and helps the system work the way it’s supposed to. Depending on how many people you need to train and how hands-on the sessions are, expect to spend anywhere from $2,000 to $10,000 to do it right.
What Makes the Cost Go Up?
DLP isn’t cheap, and the price tends to increase as you try to solve more problems. Here are the big factors that push costs higher:
- User count increases: Every new employee or contractor adds a license, especially if you monitor BYOD devices.
- Large or unstructured data environments: Lots of files, documents, and shared drives mean more scanning and tagging.
- Multiple modules or integrations: Need cloud DLP, email DLP, endpoint DLP, and data classification? You’ll pay for each.
- Heavy compliance requirements: If you’re in healthcare, fintech, or e-commerce, expect more investment in both tools and audits.
- Real-time monitoring needs: DLP systems that offer immediate blocking or alerting typically cost more than batch-based systems.
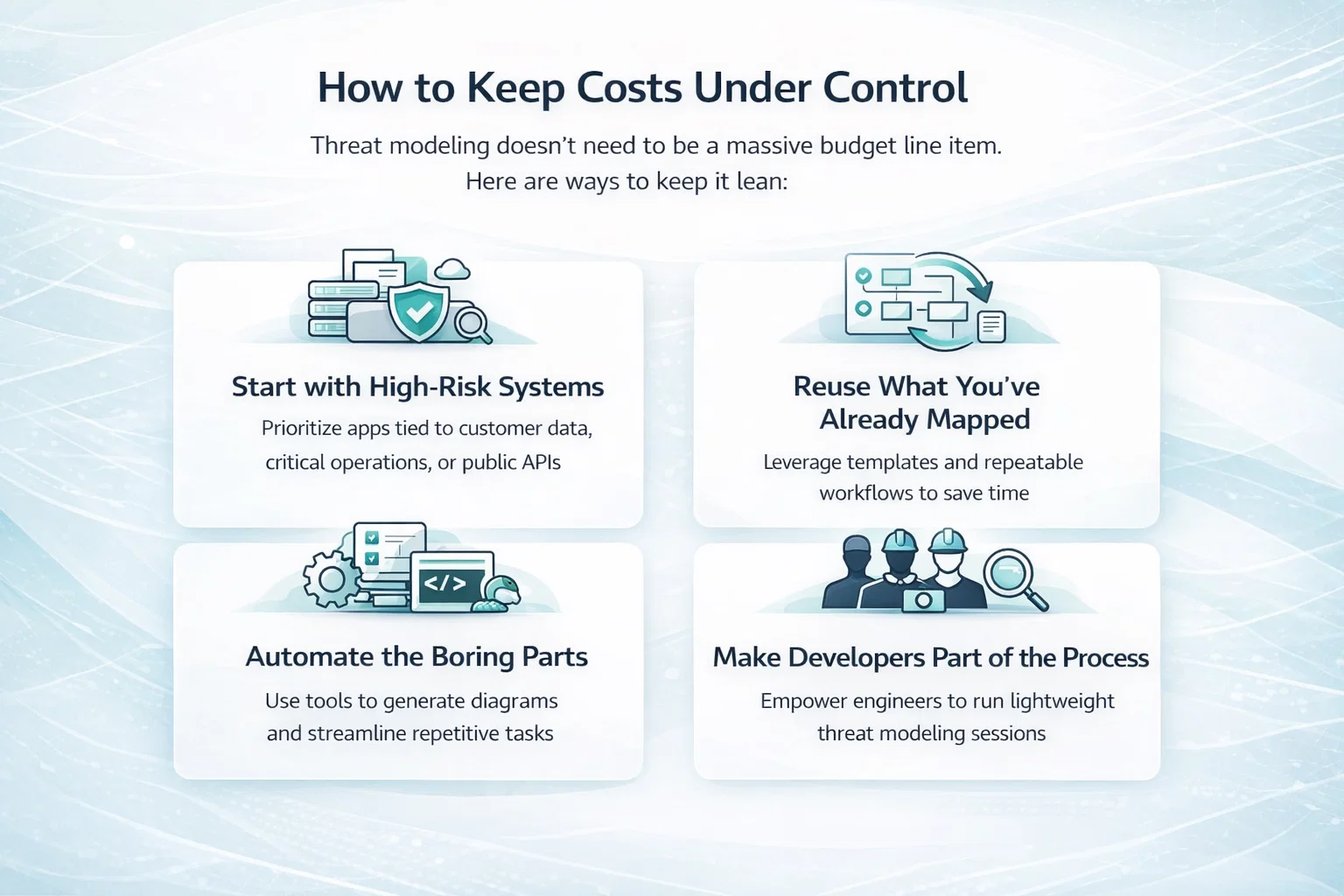
Where Businesses Overspend (and How to Avoid It)
It’s easy to get carried away, especially when dealing with compliance pressure or post-breach panic. Here’s where many companies spend more than they need to:
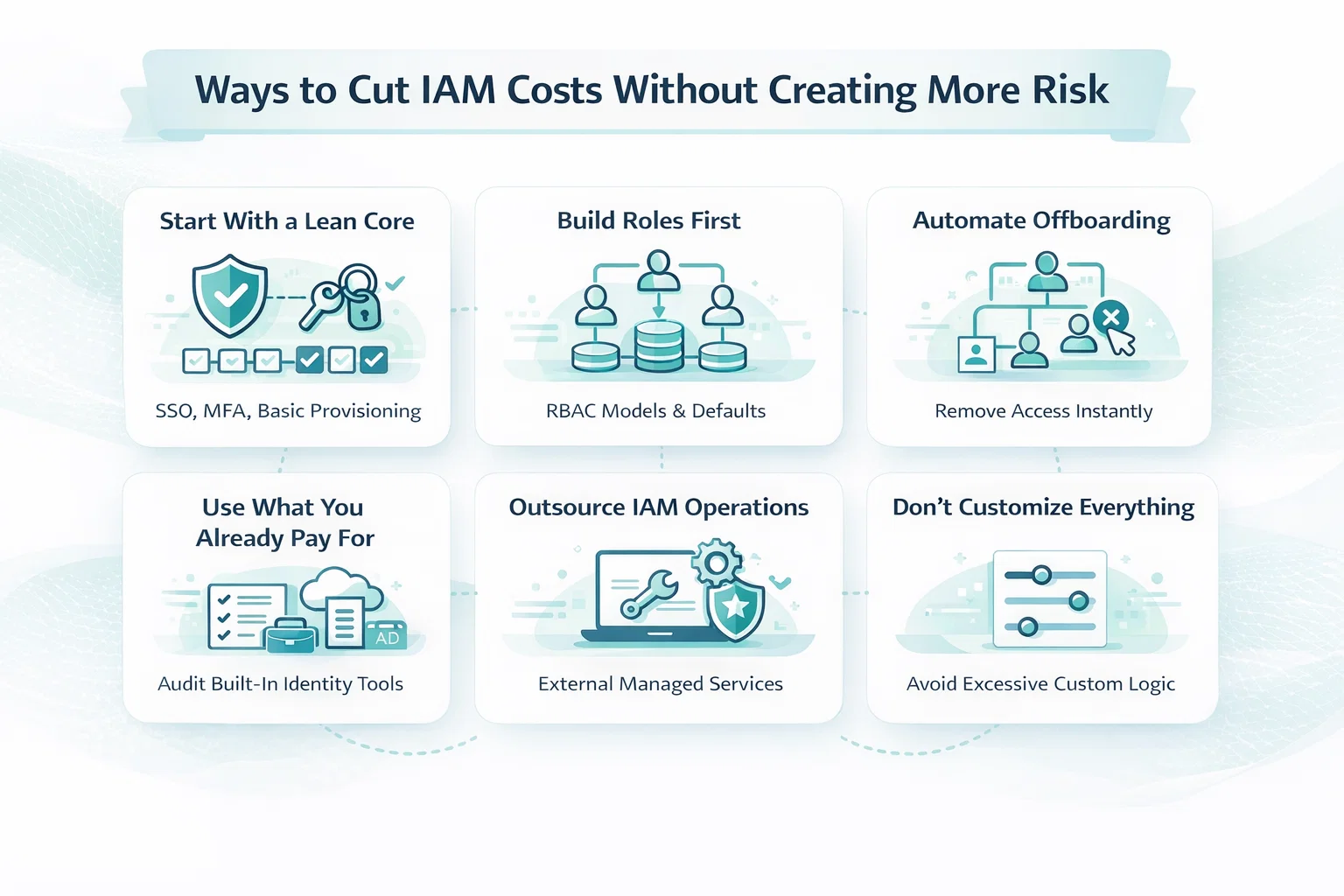
- Buying everything at once: Start small. Focus on the biggest risks first. Add more modules as needed.
- Over-customizing rules: Keep policies simple at first. Overly specific rules lead to false positives and frustrated users.
- Ignoring data volume thresholds: Some cloud-based DLP plans have hard data caps. Watch those carefully to avoid overage fees.
- Skipping planning or pilot programs: Testing with a small group helps uncover gaps before rolling out to the entire company.
What’s the Return on Investment?
It doesn’t take much for a data loss prevention solution to justify its cost. In fact, for many companies, avoiding just one serious incident more than covers the investment. A single data breach today can easily run into the millions when you factor in investigation, legal fees, customer notification, and the fallout from reputational damage.
Regulatory fines alone can be brutal, especially in industries with tight compliance rules. Even something as simple as an employee sending the wrong file to the wrong person could put customer data at risk and trigger a chain of issues. Beyond the financial hit, security incidents often cause major internal disruption – from lost productivity to burnout and erosion of trust across teams. When you stack that up against a few thousand dollars a month for reliable DLP coverage, the math becomes pretty easy to explain.

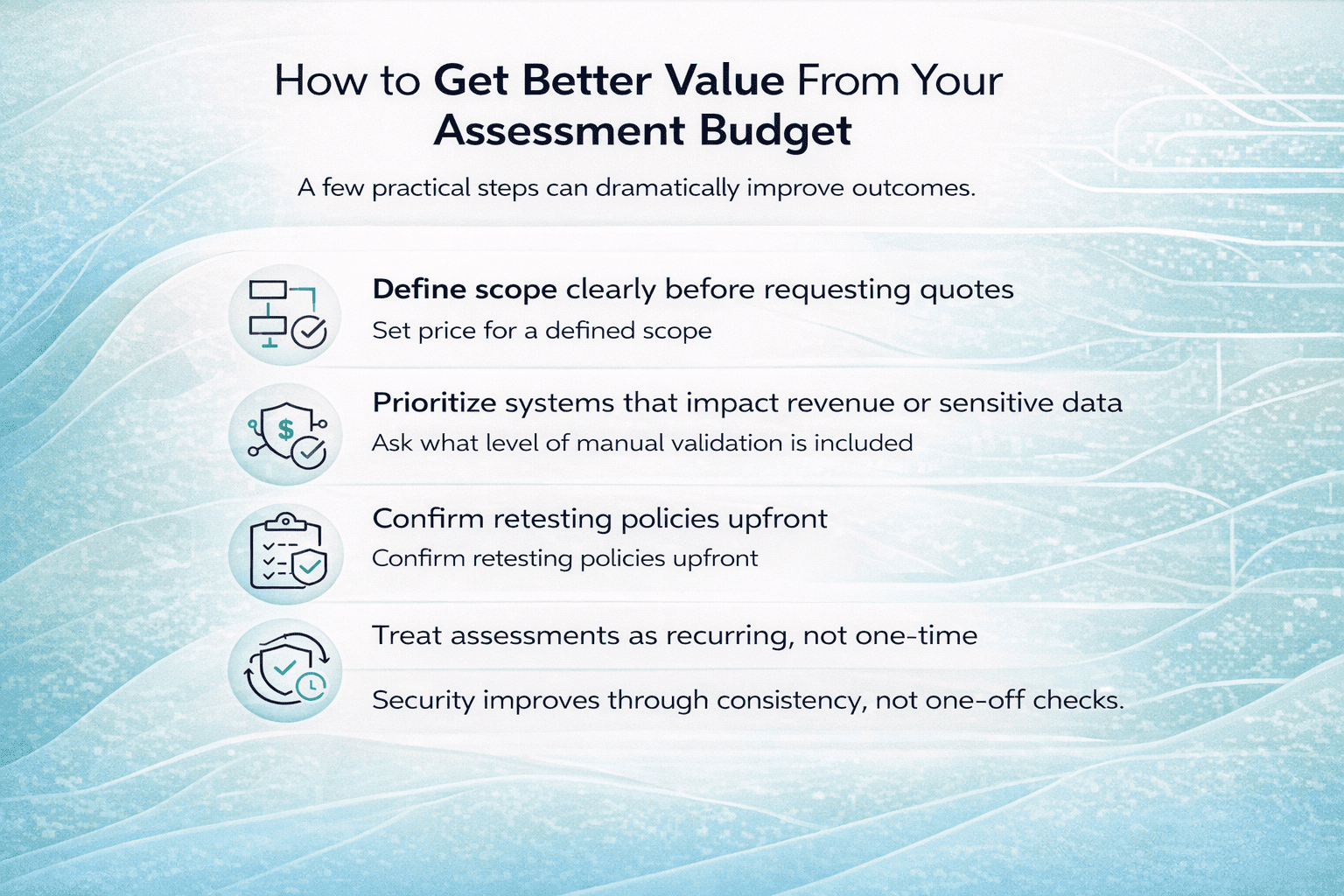
Smart Ways to Stretch Your DLP Budget
If you’re trying to get serious about data protection without draining your IT budget, here are some practical steps:
- Audit your data first: Know where your sensitive data lives, how it flows, and who touches it. This helps right-size your DLP needs.
- Start with email or endpoint monitoring: These are high-risk areas where basic DLP features bring fast results.
- Bundle features or negotiate contracts: Vendors often discount bundled tools or longer-term agreements.
- Avoid overbuilt enterprise tools if you’re an SMB: You probably don’t need forensic-level controls from day one.
- Use built-in DLP from existing platforms: Some productivity suites already include basic data protection features. Leverage those before buying extra tools.
Заключні думки
Too many companies wait until after a breach or compliance warning to take DLP seriously. And by then, it’s not a budgeting conversation anymore – it’s damage control.
You don’t have to buy the most expensive tool to get value. The trick is to start small, focus on your actual risks, and build up from there. Data loss prevention costs money, yes. But handled right, it can also save you from the kind of financial and reputational hit that’s hard to recover from.
The bottom line? Protecting your data isn’t optional anymore. But overspending on protection you don’t understand isn’t smart either. With a thoughtful approach, you can get real security without breaking the budget.
ПОШИРЕНІ ЗАПИТАННЯ
- Is data loss prevention software expensive?
It can be, but it doesn’t have to be. For small teams, DLP can start around $10 to $90 per user per year, depending on the vendor and features. The bigger costs usually come from setup, customization, and managing false alerts. That’s why it’s smart to start small, focus on your riskiest areas, and build from there.
- What’s the biggest cost driver in a DLP rollout?
People often think it’s the software license, but it’s usually the complexity. The more systems you want to monitor, the more custom rules you build, and the more alerts you want in real time, the more expensive it gets. Simpler policies and clear goals help keep costs down.
- Can I just use built-in DLP from tools we already have?
In some cases, yes. Many productivity suites offer basic DLP features like email filtering or file access controls. It’s a good starting point, especially for small businesses. Just make sure you’re not assuming it does more than it actually does.
- Do I need to hire someone full-time to manage DLP?
Not necessarily. If you’re a smaller company or using a managed service, you can usually get by with part-time oversight or vendor support. But as your setup grows more complex, having someone who understands your DLP rules and monitors alerts becomes more important.
- How long does it take to see value from DLP?
You’ll likely see impact within the first 1-2 months, especially if you’re blocking common mistakes like sending sensitive data to the wrong person. The deeper return comes over time as policies get fine-tuned and the system fits more naturally into your workflows.
- What’s the most common mistake businesses make with DLP?
Trying to do everything at once. It’s tempting to lock down every possible risk right away, but that usually leads to alert fatigue and user pushback. A phased approach almost always works better, both for cost and adoption.