Endpoint protection pricing can feel confusing on purpose. Vendors talk about features, bundles, and tiers, but rarely about what you actually end up paying or why the numbers vary so much. The truth is, endpoint protection cost depends on more than just the tool itself. It’s shaped by company size, security maturity, and how much work you expect your team to handle internally. In this article, we’ll break down what drives endpoint protection costs, what’s usually included, and where hidden expenses tend to show up.
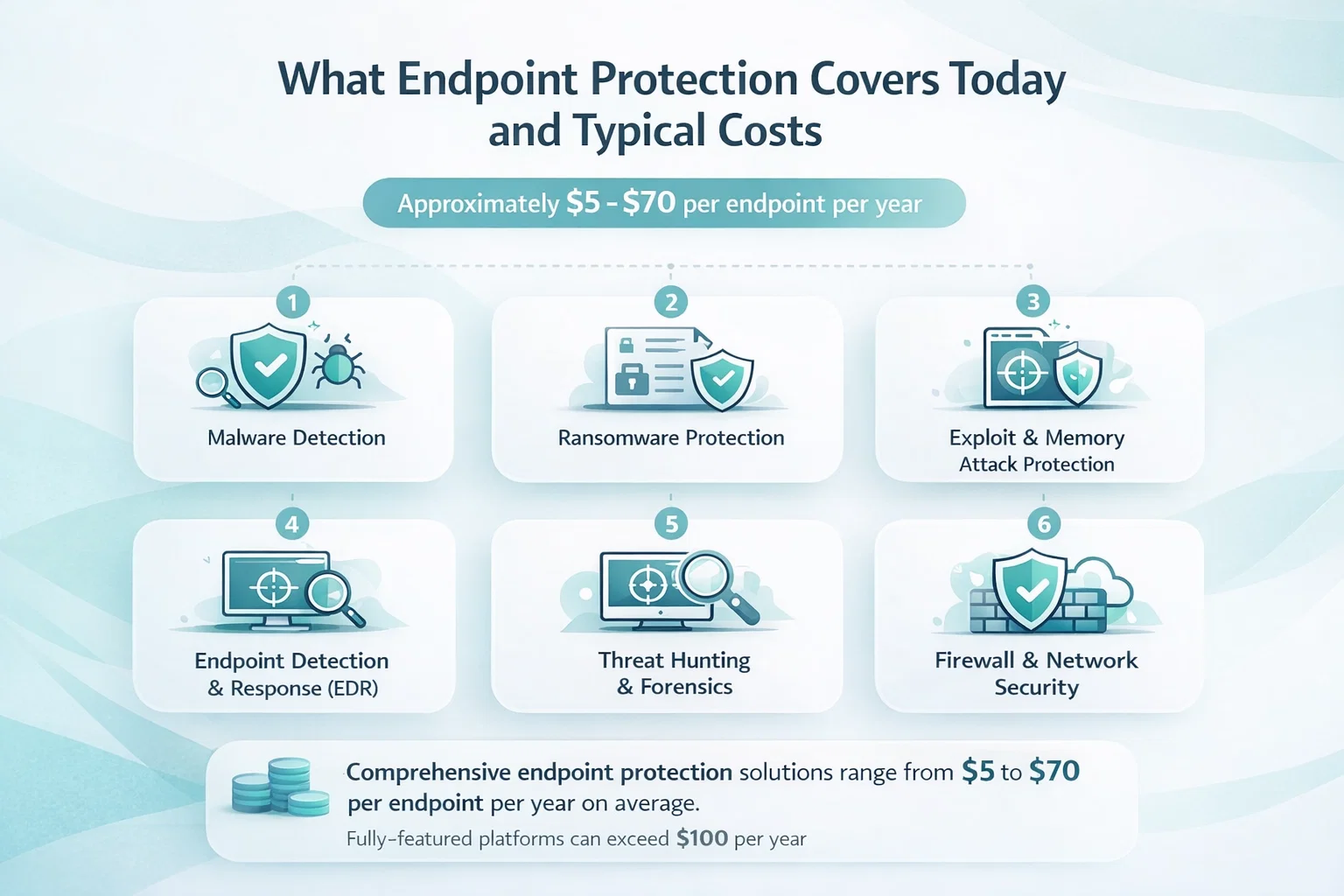
What Endpoint Protection Actually Covers Today and Typical Costs
Before diving into cost, it helps to define what “endpoint protection” means now. It’s no longer just antivirus software running quietly in the background.
Modern endpoint protection platforms typically combine several layers of defense into a single agent or suite. Depending on the vendor and tier, this can include:
- Signature-based and behavior-based malware detection
- Ransomware prevention and rollback
- Exploit and memory attack protection
- Виявлення та реагування в кінцевих точках (EDR)
- Threat hunting and forensic visibility
- Device control and application allowlisting
- Host-based firewall and network protection
- Cloud-managed policies and reporting
Some platforms go further, adding extended detection and response (XDR), identity signals, or integration with SIEM and SOAR tools. Each additional capability affects pricing, sometimes significantly.
On average, entry-level endpoint protection typically ranges from around $5 to $30 per user per month, which roughly translates to $60 to $360 per user per year at that basic tier. Mid-level or more capable endpoint protection solutions are most commonly seen in the $40 to $70 per endpoint per year range, while fully featured or enterprise offerings with advanced detection, response, and monitoring regularly exceed $100 per endpoint annually.
How We Approach Endpoint Protection at A-listware
За адресою Програмне забезпечення списку А, we look at endpoint protection as part of a bigger operational picture, not a line item tied only to software licenses. In practice, the real cost of endpoint security is shaped by how well systems are built, maintained, and supported over time. When endpoints are integrated into a stable infrastructure and managed by experienced teams, security tools work as intended and costs stay predictable. When they are not, companies often end up paying more through incidents, downtime, and constant adjustments.
We help businesses keep endpoint protection costs under control by aligning security with software development, infrastructure management, and day-to-day IT operations. Our teams integrate directly with client environments, support secure development practices, and help maintain the systems that endpoint protection platforms rely on. This reduces unnecessary spend on overlapping tools and emergency fixes. The result is a security setup where endpoint protection delivers real value without turning into an ongoing and hard-to-explain expense.
Typical Endpoint Protection Price Ranges in 2026
Let’s start with realistic, current price ranges. These are not promotional figures. They reflect what businesses actually pay across SMB, mid-market, and enterprise environments.
Entry-Level Endpoint Protection
This tier usually focuses on core malware and ransomware protection without deep investigation or response features.
- $2 to $5 per endpoint per month
- $20 to $50 per endpoint per year
Common for:
- Small businesses
- Basic compliance requirements
- Environments with limited internal IT security resources
Mid-Tier Endpoint Protection with EDR
This is where most growing companies land. EDR adds visibility, telemetry, and the ability to investigate incidents.
- $5 to $12 per endpoint per month
- $60 to $140 per endpoint per year
Common for:
- SaaS companies
- Distributed teams
- Regulated industries with audit pressure
Advanced Endpoint Protection and XDR
This tier bundles endpoint security with identity, email, or network signals, often managed from a single console.
- $12 to $25+ per endpoint per month
- $150 to $300+ per endpoint per year
Common for:
- Enterprises
- Security-mature organizations
- Companies with 24/7 monitoring or SOC operations
These are software costs only. They don’t include deployment effort, internal labor, or optional managed services.
Pricing Models You’ll Encounter (And What to Watch For)
Endpoint protection vendors don’t all price the same way. Understanding the model matters just as much as the number. Here’s a practical breakdown:
| Pricing Model | How It Works | Плюси | Мінуси |
| Per-Endpoint Subscription | You pay for each protected device, usually billed annually, sometimes shown with monthly equivalents. | Predictable budgeting; scales linearly with headcount | Virtual machines and short-lived devices still count; can get expensive in VDI or cloud-heavy environments |
| Per-User Licensing | Some vendors charge per user instead of per device. | Works well if users have multiple devices; easier for remote-first teams | Shared workstations complicate counts; service accounts and automation users may still need coverage |
| Tiered Feature Bundles | Features grouped into plans such as “Core,” “Advanced,” and “Complete.” | Clear upgrade path; easier comparison inside one vendor | You often pay for features you don’t use; critical capabilities may be locked behind higher tiers |
| Enterprise Agreements | Large organizations negotiate custom contracts. | Volume discounts; predictable multi-year pricing | Less flexibility; overbuying is common |
Endpoint Protection vs Managed Endpoint Security Costs
Software alone only covers part of the story. Many organizations pair endpoint protection with managed services to make sure threats are not just blocked, but actively monitored and responded to.
Managed Detection and Response, or MDR, adds human analysts to the mix. These experts watch alerts, validate threats, and guide-or even take-action when incidents occur. Pricing typically ranges from $15 to $40 per endpoint per month, and most MDR services assume you already have a compatible EDR platform in place. What you get in return is continuous oversight: round-the-clock monitoring, thorough threat validation, and guidance on incident response. For smaller teams, MDR can actually be more cost-effective than building a full internal security operation.
Fully managed endpoint security takes it a step further. These services combine software, monitoring, tuning, and incident response into one package, with prices usually between $25 and $60+ per endpoint each month. This level of service is especially useful when internal security staff is limited, risk tolerance is low, or regulatory requirements demand constant vigilance.
In short, MDR is ideal for teams that need expert guidance without hiring full-time staff, while fully managed endpoint security suits organizations that want end-to-end coverage without the overhead of internal management. Both approaches shift costs from reactive firefighting to proactive protection, making spending predictable while reducing the chances of expensive incidents.
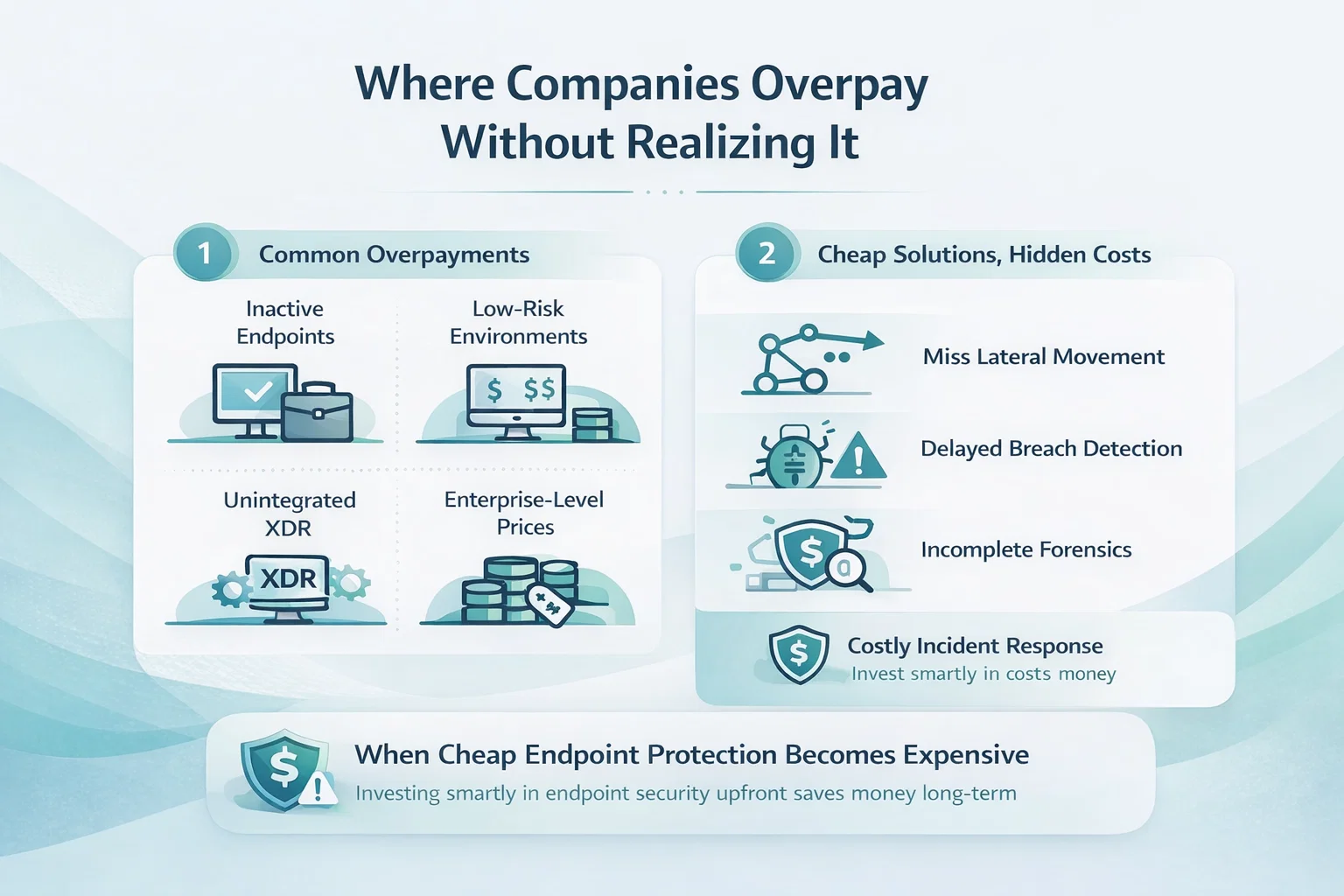
Where Companies Overpay Without Realizing It
Overpaying for endpoint protection is common. Companies sometimes pay for EDR on devices that never leave the office, license inactive endpoints, overbuy XDR features that aren’t integrated, or pay enterprise-level prices for low-risk environments. Reviewing licenses quarterly can save thousands, yet it’s often overlooked.
On the flip side, cheap solutions can be deceptively expensive. Underpowered tools may miss lateral movement, delay breach detection, or leave gaps in forensic data. A single serious security incident can erase years of software savings, which is why investing appropriately upfront often saves money in the long run.
When Cheap Endpoint Protection Becomes Expensive
The cheapest quote upfront isn’t always the most economical choice. Cutting corners with underpowered tools can lead to hidden costs that hit hard later. Threats can move laterally across your network without being noticed, breaches may take longer to detect, and forensic data might be incomplete when you need it most. In many cases, organizations end up calling in incident response consultants at the worst possible moment. One major security incident can easily erase years of perceived savings on software licenses.
Endpoint Protection Cost Scenarios
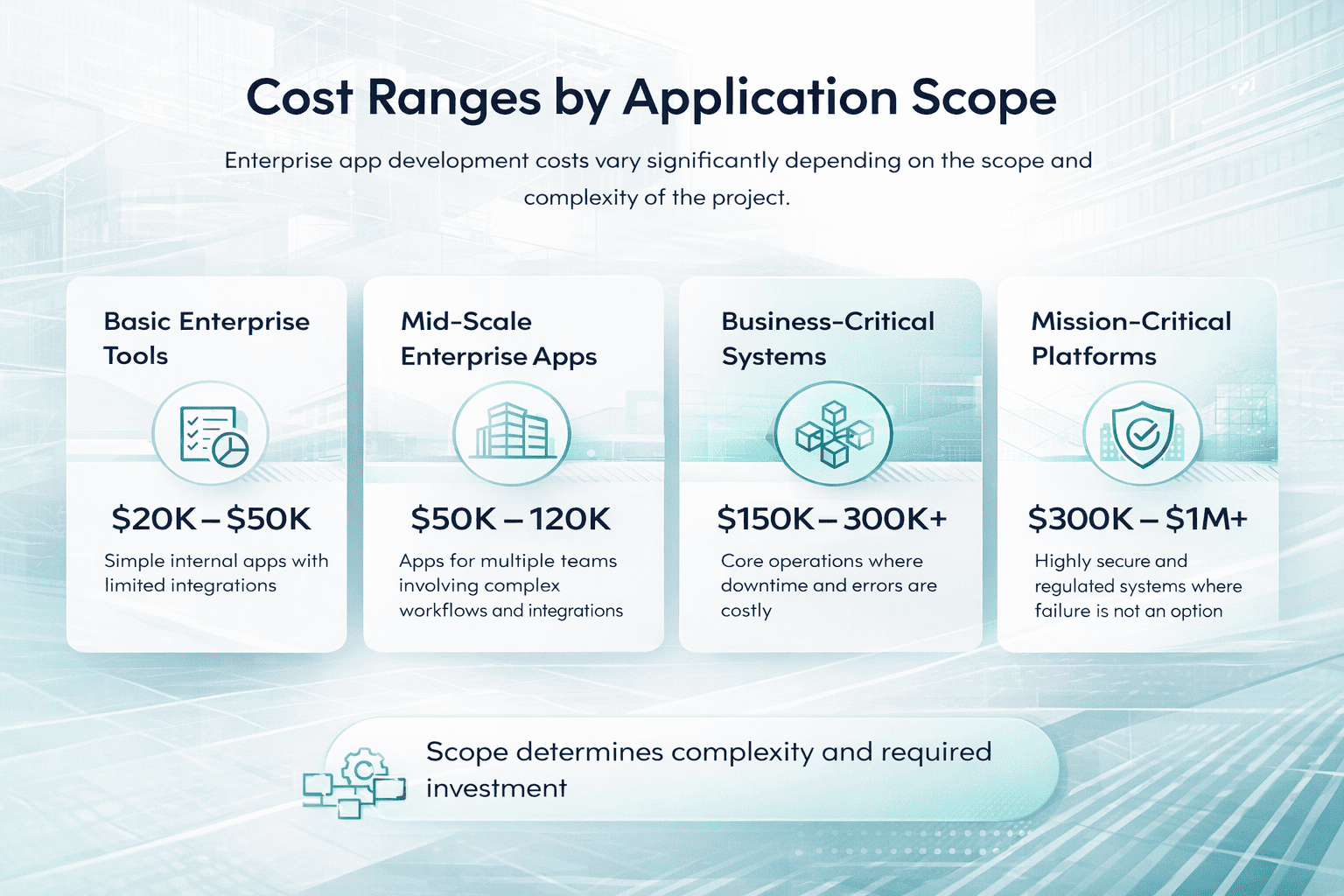
Here are realistic annual cost examples to ground expectations.
- 25-person startup, laptops only, basic protection: $750 to $1,500
- 100-person remote company with EDR: $8,000 to $14,000
- 500-endpoint mixed environment with servers and MDR: $90,000 to $180,000
- Enterprise with XDR and SOC integration: $250,000+
Actual numbers depend on vendor, negotiation, and scope clarity.
Заключні думки
Endpoint protection cost looks simple on pricing pages but complex in real life. The real expense is shaped by how many devices you protect, how deeply you want visibility, and who carries the responsibility when something goes wrong.
Treat endpoint security as a system, not a SKU. Budget with intention. Ask uncomfortable questions during demos. And remember that prevention is cheaper than cleanup, but only if it actually works.
If you plan carefully, endpoint protection doesn’t have to be a runaway cost. It becomes a controlled, measurable investment in keeping your business running when threats inevitably knock on the door.
ПОШИРЕНІ ЗАПИТАННЯ
- Why do endpoint protection prices vary so much between vendors?
Because vendors are selling different things under similar names. Some focus purely on prevention, others bundle detection, response, monitoring, or even managed services. Pricing also reflects how much work is expected from your internal team versus the vendor. - Is cheaper endpoint protection always a bad idea?
Not necessarily. For small teams with limited risk exposure, a simpler and lower-cost solution can be enough. Problems start when companies choose a cheaper tool but expect enterprise-level coverage without the staff or processes to support it. - How many endpoints do vendors usually count for pricing?
Most vendors price per endpoint or per user, but definitions differ. A laptop and a virtual machine might be counted separately, and temporary or shared devices can complicate the numbers. It is worth clarifying this before committing to a contract. - Does endpoint protection cost include incident response?
In most cases, no. Basic plans usually cover detection and alerts, but investigation and response are either limited or handled internally. Full response support often comes with higher-tier plans or managed services. - Can endpoint protection replace a security team?
Tools help, but they do not replace people. Automation can reduce workload, yet someone still needs to review alerts, tune policies, and make judgment calls. Endpoint protection lowers effort, but it does not eliminate responsibility. - How often should endpoint protection budgets be reviewed?
At least once a year, or whenever the business changes significantly. Growth, new devices, cloud migration, or regulatory pressure can all shift what level of protection is actually needed, and that directly affects cost.