Threat modeling often sounds like a heavy security exercise that only large enterprises can afford. In reality, the cost of threat modeling depends less on company size and more on how thoughtfully it is approached. Some teams overpay by turning it into a slow, manual process. Others skip it entirely and pay far more later through rework, delays, or security incidents.
This article takes a grounded look at threat modeling cost from a practical business perspective. Not theory, not inflated promises. Just a clear breakdown of where the time and money actually go, what influences the final cost, and how to think about threat modeling as part of everyday product and system design rather than a one-off security checkbox.
What Is Threat Modeling, Really, and What Is Its Cost?
Threat modeling gets mentioned a lot in security conversations, but people often mean different things when they say it. At its core, it’s about getting ahead of problems by thinking through how a system might be attacked before anything actually goes wrong. It’s not about reacting after the fact. It’s a structured way to ask: what could break here, how likely is it, and what can we do about it?
When done properly, threat modeling helps teams catch design issues early – before a single line of code is written. That might be something like an open API with no access controls or murky trust boundaries between services. It’s not just about patching vulnerabilities. It’s about understanding how things work together, how assumptions could be broken, and how attackers might move through the system in unexpected ways.
The process usually involves a few key steps: figuring out what needs protecting, mapping how data moves, identifying weak spots, and deciding what should change. It won’t give you perfect answers, but it gives your team a clearer picture of the risks so they can address them early, and early always costs less than late.
Depending on how you approach it, costs can vary widely: internal efforts might run a few thousand per person for training and tools, consultant-led projects often fall between $10,000 and $100,000, and managed platforms typically are around $5,000 per month.
The Real Question: What Do You Want Out of Threat Modeling?
Before we talk numbers, it’s worth asking: what’s the point of doing threat modeling in your environment?
Because the answer changes everything. If you’re trying to tick a compliance box, the effort (and cost) will look different than if you’re integrating security into your design culture. Some teams just need a one-time analysis for a high-risk app. Others are looking to train developers, build out reusable threat libraries, and catch systemic risks early.
Cost depends heavily on scope:
- Single project vs. ongoing program
- Manual whiteboarding vs. automated modeling tools
- Security team-led vs. cross-functional ownership
So the real cost is tied to your ambitions, not just your budget.
Secure Development Support at A-listware
Au Logiciel de liste A, we don’t frame security measures as a separate product or standalone service. Instead, it’s something our engineers support when building secure software for clients. Because we provide development teams that include cybersecurity expertise, threat modeling naturally fits into broader work on system design, architecture, and security review.
We don’t list threat modeling as a one-off engagement or sell it as a fixed package. What we offer is flexible support that matches how clients run projects. That might include modeling threats early in development, evaluating changes before a release, or embedding security thinking into CI/CD pipelines. How much time or cost this takes depends on the scope and maturity of the client’s systems.
Threat Modeling, Engagement Models, and Cost Structures
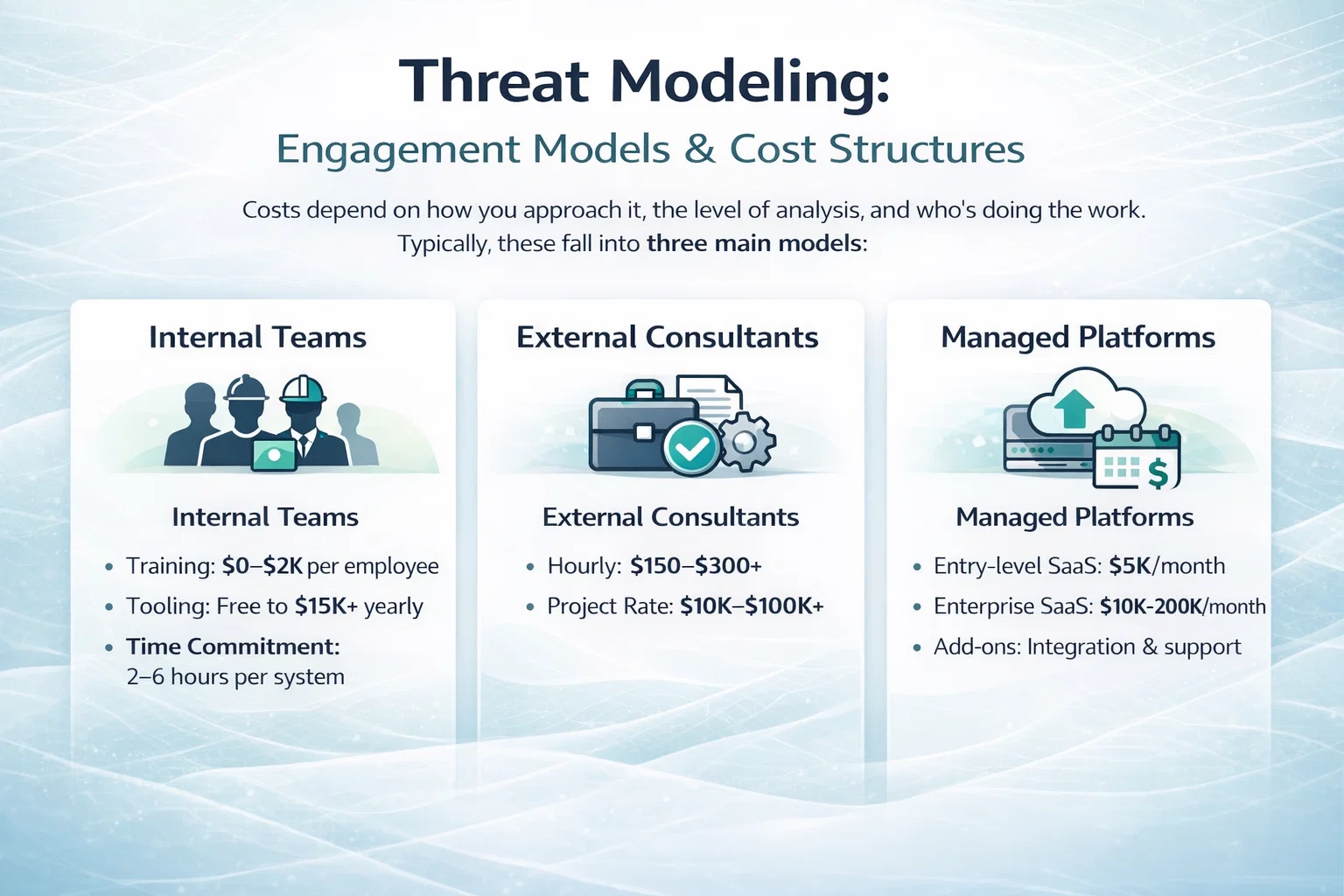
There’s no universal price tag for threat modeling. What you end up paying depends heavily on how you approach it, the depth of analysis you need, and who’s actually doing the work. Broadly speaking, threat modeling services fall into three main engagement models: internal teams, external consultants, and managed platforms. Each has its own cost implications, trade-offs, and fit depending on your business maturity and goals.
Internal Teams: In-House or Augmented Staff
Running threat modeling internally means leveraging your own developers, architects, and security team. It’s often the most cost-effective option on paper, especially for companies with existing security talent. But the true cost isn’t just salary – it’s time. You’re trading engineering hours for risk visibility.
For organizations new to threat modeling, internal ramp-up often includes structured training. Instructor-led courses can range from $500 to $2,000 per person depending on complexity. Tooling costs also vary widely.
The biggest hidden cost here is opportunity. Pulling senior engineers into workshops or diagram reviews during key development phases can slow down delivery. That said, teams who build this muscle internally can eventually scale the practice with very little external spend. For mature teams, the cost is mainly time, and that’s often a worthwhile trade.
Typical internal program costs:
- Time commitment: 2-6 hours per system, depending on complexity.
- Training: $0 – $2,000 per team member.
- Tooling: Free to $15,000+ annually for licensed platforms.
External Consultants: Focused Expertise and Audit-Ready Results
When internal resources are stretched or when an outside perspective is critical, hiring an external threat modeling consultant can bring speed and clarity. These professionals are typically brought in to assess a high-risk system, support a security review, or prepare for compliance audits.
Rates vary based on experience and scope. Independent consultants or boutique firms typically charge between $150 and $300 per hour. Project-based work for a full threat modeling engagement, especially one involving system decomposition, stakeholder workshops, and mitigation strategy, can range from $10,000 to over $100,000.
This model is ideal for organizations facing regulatory pressure, dealing with sensitive data, or requiring a formal security architecture review before deployment. You’re paying for speed, assurance, and audit-grade documentation.
Typical consultant engagement costs:
- Hourly: $150 – $300+
- Fixed project rate: $10,000 – $100,000
Managed Threat Modeling Platforms: Tools, Templates, and Scale
For companies building a long-term, scalable threat modeling practice across many teams, managed platforms or SaaS tools offer a structured, repeatable path. These platforms integrate with your DevOps or SDLC pipelines and often come with templates, asset libraries, and risk scoring systems.
Subscriptions are typically priced monthly and may be tiered based on usage, project volume, or compliance requirements. Entry-level plans start around $5,000 per month, but enterprise-scale deployments with full integration and support can run $20,000 or more monthly.
The trade-off here is twofold: the upfront investment in tooling and the internal work required to drive adoption. If developers don’t use the platform, it becomes shelfware. But when paired with internal champions and good training, managed platforms can drastically reduce per-project costs by automating documentation, surfacing risks earlier, and improving consistency.
Typical platform-based costs:
- Entry-level SaaS: $5,000/month.
- Enterprise SaaS with full DevSecOps integration: $10,000 – $20,000/month.
- Add-ons: onboarding, workflow integration, support.
Threat Modeling Cost Comparison by Engagement Model
| Engagement Model | Typical Costs | Best For | Key Trade-Offs |
| Internal Teams | Training: $0 – $2,000 per person
Tools: Free to $15,000+/year |
Teams with in-house security talent or looking to build it | Slower delivery due to time demands on devs and architects |
| External Consultants | Hourly: $150 – $300+
Projects: $10,000 – $100,000 |
Compliance-heavy projects or critical systems | Higher cost, but faster delivery and audit-grade assurance |
| Managed Platforms (SaaS) | Entry: $5,000/month
Enterprise: $10,000 – $20,000/month |
Organizations scaling threat modeling across many teams | Upfront investment plus the challenge of driving adoption |
What Affects the Cost (and What to Watch Out For)
Whether you do it in-house or bring in help, a few things will push the cost up or down:
1. System Complexity
Threat modeling a small web app is one thing. Modeling a distributed microservices architecture with sensitive PII flowing across APIs and cloud storage? That’s a bigger lift.
- More entry points = more attack surfaces
- More data = more privacy concerns
- More integrations = more unknowns
The more moving parts, the more time you’ll need to decompose the system and map threats accurately.
2. Industry Requirements
If you’re in healthcare, finance, or government, you can’t just say “we thought about security” and move on. You’ll probably need documented models that align with compliance standards (HIPAA, PCI, GDPR, etc.). That adds effort, and often consultants or auditors.
3. Tooling
Free tools work fine for small teams or those just starting out. But enterprise-grade tools with automation, dashboards, and templates cost money, and often come with a licensing or training investment.
Choose tools based on who’s going to use them. If your developers hate the interface, it doesn’t matter how smart the backend is.
4. Maturity of Your Teams
Security-savvy engineers need less hand-holding. If your team is just starting to learn threat modeling, you may need to factor in training, onboarding, and more time in the early stages. Long term, though, that investment pays off by reducing reliance on security bottlenecks.
Is It Worth the Cost? Let’s Talk ROI
This is where things get interesting. Threat modeling doesn’t just cost you time and money. It saves you time and money too – sometimes a lot.
Here’s what it helps prevent:
- Costly rework due to late-stage security fixes.
- Production incidents caused by overlooked risks.
- Regulatory fines due to missed controls.
- Brand damage from preventable breaches.
Example ROI Scenario
Let’s say a 2-hour modeling session finds a design flaw that would’ve taken 100 hours to fix post-release. If your engineers cost $100/hour, that’s $10,000 saved from a $200 investment. That’s a 4,900% return. And that’s not rare.
The earlier you catch issues, the cheaper they are to fix. Threat modeling is one of the few practices that moves that “fix window” as far left as possible.
What Are You Actually Paying For?
Threat modeling isn’t just a diagram or a checklist. You’re paying for:
- Time spent mapping the system and identifying threats.
- Expertise in recognizing non-obvious attack paths.
- Collaboration between teams (security, dev, product).
- Documentation that can be reused for audits or future iterations.
- Mitigation recommendations that reduce real-world risk.
If you treat it like a one-time security exercise, it’s expensive. But if you treat it like an embedded practice that saves effort down the line, it becomes an efficiency tool.
Comment maîtriser les coûts
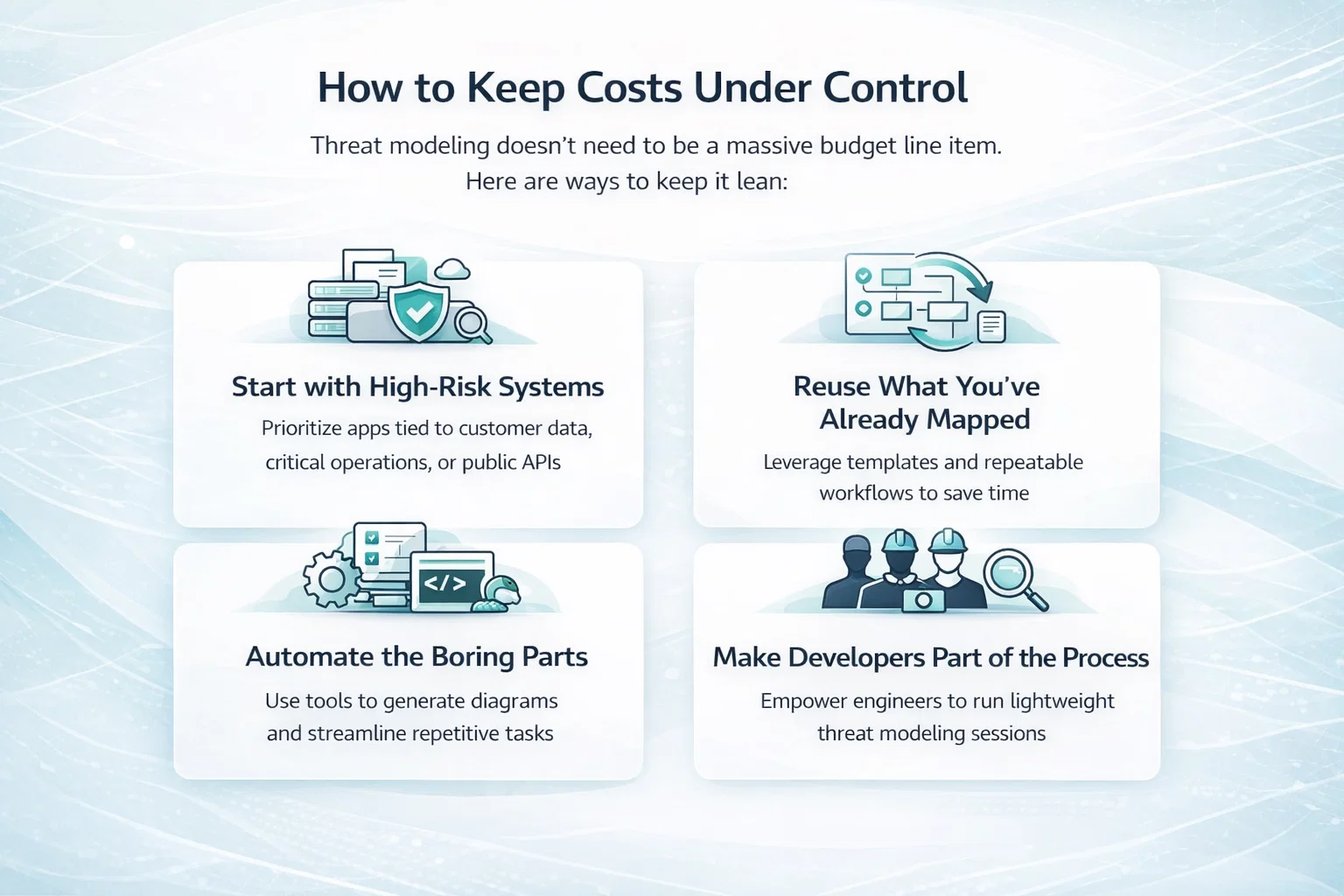
Threat modeling doesn’t need to be a massive budget line item. Here are ways to keep it lean:
Start with High-Risk Systems
Don’t try to threat model every system out of the gate. Focus first on the applications that really matter – the ones tied to customer data, critical operations, or revenue streams. APIs exposed to the public internet are another good place to start. These are the areas where a missed threat can do real damage.
Reuse What You’ve Already Mapped
Once you’ve built a few models, you’ll start to notice patterns. Maybe it’s the same login flow or data sync logic repeating across services. Reuse those pieces. Create templates for shared components or standard workflows. It saves time and helps keep things consistent without starting from scratch each time.
Automate the Boring Parts
Tools can speed up a lot of the heavy lifting. Diagram generation from code, threat libraries, and pre-built checklists can all help. Just remember: automation is a support tool, not a substitute for thinking. Use it to move faster, not to avoid critical judgment.
Make Developers Part of the Process
Threat modeling isn’t just a security job. It works best when developers are comfortable running lightweight sessions themselves. Give them basic training, a few examples, and room to try it. Let security review the outputs instead of owning the whole process. That shift makes the practice scale across teams.
Keep Workshops Lean and Useful
Formal reviews aren’t always necessary. Sometimes a 30-minute whiteboard session during sprint planning is enough to spot obvious gaps or design issues. Aim for just enough structure to be useful without slowing things down. Lightweight, recurring discussions tend to be more effective than rare, heavyweight audits.
When to Spend More
There are times when higher investment is justified:
- Launching a public-facing product in a regulated industry.
- Refactoring a legacy system with unclear data flows.
- Handling personal or financial data at scale.
- Building security into a CI/CD pipeline with compliance dependencies.
In those cases, threat modeling isn’t optional. It’s the foundation of responsible design and a way to avoid firefighting six months down the line.
Réflexions finales
If you’re trying to figure out how much to budget for threat modeling, start with this question: “What would it cost you if something went wrong?”
Because the cost of threat modeling isn’t just what you spend on sessions, tools, or consultants. It’s the opportunity to prevent things that cost far more – outages, breaches, rework, and reputation loss.
Treat it like a strategic investment, not an audit checkbox. The best teams don’t ask “how much will this cost?” They ask, “what’s the cost of not doing it?”
And more often than not, that answer is much higher.
FAQ
- Is threat modeling expensive?
It depends on how you approach it. If you’re bringing in external consultants for a full deep-dive after a product is already live, yes, it can get pricey. But when baked into the development process early on, the cost is usually lower and spread out over time. In most cases, it ends up saving money by helping you catch issues before they turn into bigger problems.
- Can small teams afford threat modeling?
Absolutely. You don’t need a giant security budget to do it well. Lightweight threat modeling sessions using tools or simple whiteboarding can go a long way. The key is doing it consistently and making sure someone is responsible for following through on the findings.
- What’s the biggest factor in threat modeling cost?
Time and scope. The more complex your system, the longer it takes to map out potential threats. If your team isn’t familiar with security models or doesn’t have a clear process, that adds time too. Using experienced people and setting a realistic scope helps keep it efficient.
- Do I need to hire a security consultant just for this?
Not always. If your in-house devs or architects understand secure design, they can often lead basic threat modeling sessions. That said, for high-risk apps or compliance-heavy industries, bringing in a security partner might be worth it for peace of mind and deeper insight.
- How often should we run threat modeling?
Ideally, anytime you’re adding major features, changing infrastructure, or releasing something new. It’s not a one-and-done thing. Think of it like code review but for security risks. The cadence depends on how fast you ship and how sensitive your app is.
- Is threat modeling worth it for non-tech businesses?
If you’re building or managing any kind of digital system that holds sensitive data, yes. Even if tech isn’t your core business, the risk still lands on your lap when something goes wrong. Threat modeling is about seeing those risks ahead of time and deciding how much you’re willing to accept.


