A lot of companies ask, “How much should we budget for a vulnerability assessment?” The frustrating answer is: it depends. But that doesn’t mean you need to guess.
Whether you’re a startup doing your first scan or an enterprise juggling compliance audits, the cost comes down to scope, methodology, and what kind of visibility you actually need. In this guide, we’ll break down the pricing landscape in plain language – no scare tactics or buzzwords – just a practical look at what you’ll pay, why it varies so much, and what kind of return you can expect from doing it right.
What Is a Vulnerability Assessment and What Does It Usually Cost?
A vulnerability assessment is a structured review of your systems, applications, and networks to identify weaknesses that attackers could exploit. These weaknesses may include unpatched software, insecure configurations, exposed services, or outdated components.
The goal is not just to list issues, but to prioritize them based on risk, so teams can focus on what actually matters.
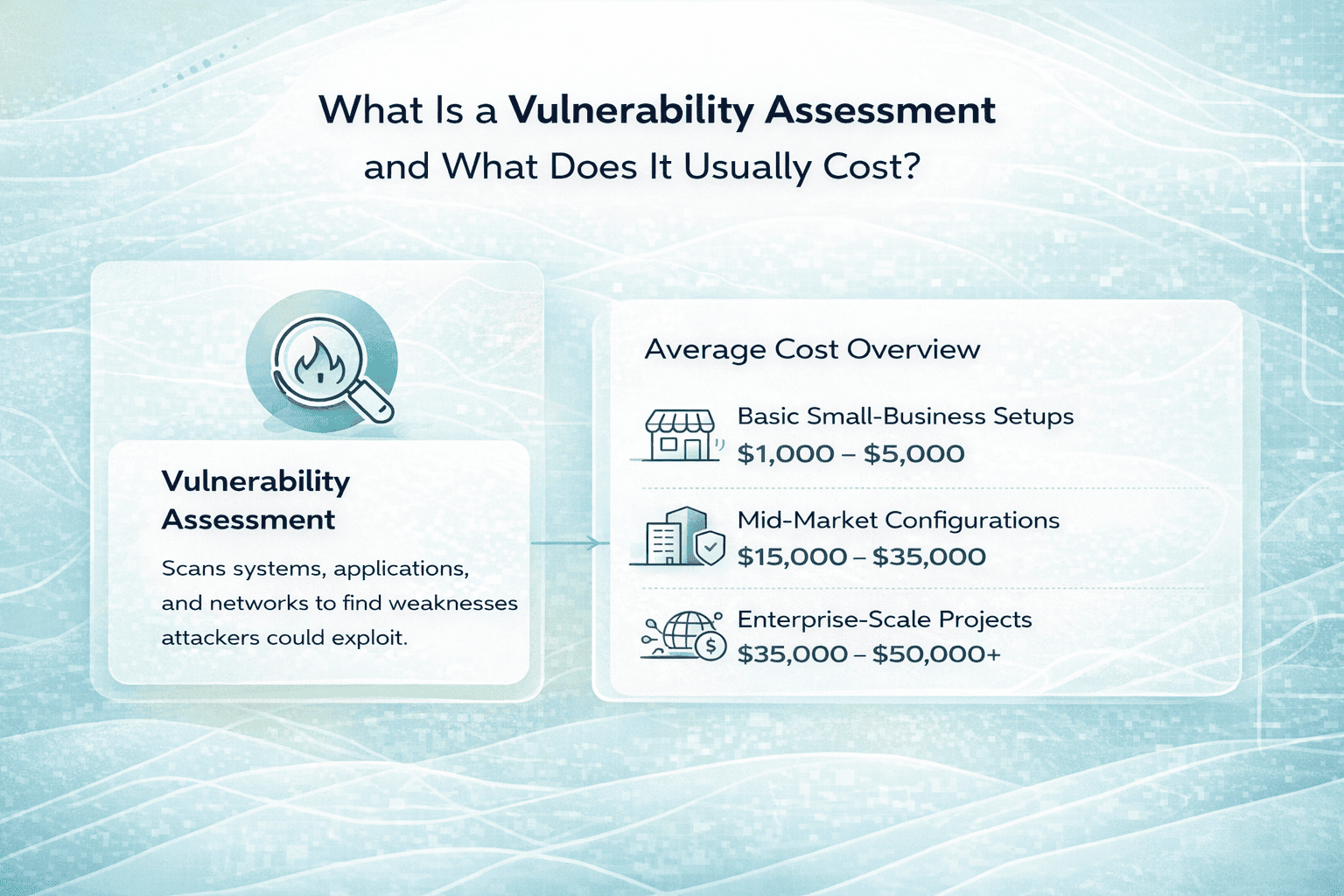
Average cost overview:
- Basic small-business setups: $1,000 to $5,000
- Mid-market configurations: $15,000 to $35,000
- Enterprise-scale projects: $35,000 to $50,000+
Most small and mid-sized businesses land somewhere in the middle. Very low prices usually mean shallow testing. Very high prices usually reflect large environments, compliance needs, or deep manual work.
How We Look at Vulnerability Assessments in Real Projects
Au Logiciel de liste A, we work closely with companies that deal with vulnerability assessments not as an abstract security exercise, but as part of real software delivery and infrastructure operations. Over the years, we have seen that the cost of an assessment rarely causes problems on its own. Issues usually appear when assessments are disconnected from development workflows, infrastructure management, or day-to-day engineering decisions. In those cases, even a well-priced assessment can turn into a sunk cost.
Our teams are involved across software development, testing and QA, infrastructure services, and cybersecurity support. This gives us a practical view of how vulnerabilities are introduced and how they are realistically fixed. From that perspective, vulnerability assessments make the most sense when they are scoped around actual systems in use – applications, cloud environments, integrations, and internal tools – rather than generic checklists. Clear scoping upfront is one of the biggest factors that keeps assessment costs under control and outcomes useful.
Why Vulnerability Assessment Pricing Varies So Much
Unlike buying software licenses, vulnerability assessments are not a fixed product. They are a service shaped by your environment and your risk profile.
Several factors drive pricing.
Scope and Asset Count
This is one of the biggest factors that influences the final price. The more systems, endpoints, and environments you want to include in the assessment, the more time and effort it takes to do it properly. Scope often covers things like internal and external networks, cloud infrastructure, databases, web applications, and any APIs you rely on. Testing a simple marketing website is very different from testing a SaaS platform with multiple integrations, user roles, and dynamic features. As the footprint grows, so does the complexity, which naturally drives up the cost.
Depth of Testing
Not every assessment goes to the same depth. Some stick to scanning for known vulnerabilities and stop there, while others go further by validating what those findings mean in context. In more advanced engagements, the team may simulate actual attack paths to understand what a real-world threat actor could exploit. This deeper approach requires more time and far more skill. Automated tools can only go so far, and the moment you need human analysis layered on top, the cost starts to reflect that.
Testing Methodology
The way an assessment is carried out plays a big role in determining price. Black box testing, where the assessor has no internal knowledge of the system, takes longer and often costs more because they have to start from scratch. Grey box testing offers a balance by giving the tester partial access or credentials, which helps them dig deeper without being totally in the dark. White box testing gives full internal access and allows for more comprehensive coverage, though it usually requires closer coordination with your internal teams. The more realistic and informed the testing, the more value you get but it also raises the cost.
Experience of the Testing Team
You’re not just paying for the time someone spends running a scanner. You’re paying for their judgment, insight, and ability to tell the difference between a cosmetic flaw and a serious security issue. Experienced testers with credentials and hands-on track records bring a level of precision that cheaper, automated services usually miss. They know how to spot complex issues that involve chained vulnerabilities, cut through noisy data, and focus your attention on what’s actually risky. That depth of knowledge is what separates a report you can act on from one that just adds confusion.
Compliance and Regulatory Requirements
When your assessment is tied to regulatory compliance, the expectations change. Standards like PCI DSS, HIPAA, or SOC 2 require specific testing methodologies, clear documentation, and structured, audit-ready outputs. Meeting those standards takes more time and often requires working with professionals familiar with the frameworks. This is about more than just checking for open ports or outdated software – it’s about producing evidence that holds up in an audit. That extra layer of rigor is necessary but also adds to the total cost.
Typical Vulnerability Assessment Costs
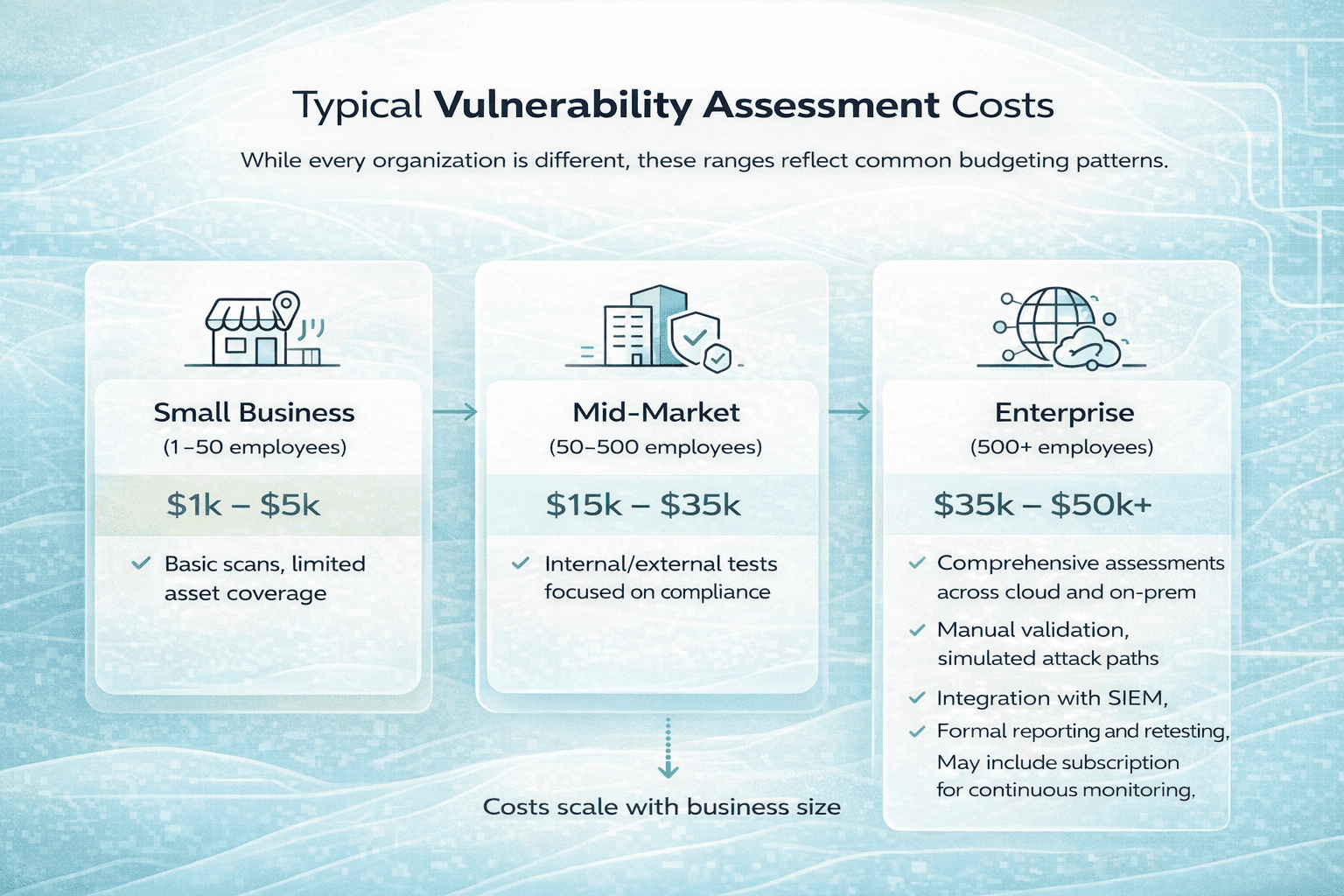
While every organization is different, these ranges reflect common budgeting patterns.
| Business Size | Typical Annual Spend | What This Usually Covers |
| Small Business (1-50 employees) | $1,000 to $5,000 | Basic automated vulnerability scanning, limited asset coverage (e.g., website or small internal network), basic reporting. Usually handled by MSP or subscription-based tools. |
| Mid-Market (50-500 employees) | $15,000 to $35,000 | Multiple internal/external scans, some manual validation, compliance-focused testing (e.g., HIPAA, SOC 2), risk prioritization. Often includes fixed-scope engagements with periodic reviews. |
| Enterprise (500+ employees) | $35,000 to $50,000+ | Comprehensive assessments across cloud and on-prem, manual validation, simulated attack paths, integration with SIEM, formal reporting and retesting. May include subscription for continuous monitoring. |
These figures represent approximate annual security testing budgets that may include multiple vulnerability assessments and penetration tests, not the cost of a single vulnerability assessment engagement.
What You Actually Get at Different Price Levels
Understanding what is included helps avoid disappointment.
Low-cost Assessments ($1,000 to $2,000)
These typically include:
- Automated scanning.
- Broad vulnerability detection.
- Limited prioritization.
What is often missing:
- Manual validation.
- Business context.
- Clear remediation guidance.
They are useful as a baseline, but rarely enough on their own.
Mid-range Assessments ($2,000 to $5,000)
This is where most organizations find value.
Usually includes:
- Internal and external scanning.
- Some manual review.
- Risk-based prioritization.
- Clear reporting.
For many teams, this level provides actionable insight without overinvestment.
High-end Assessments ($10,000+)
These often fall under penetration testing and may include:
- Manual exploitation and testing.
- Deep validation of identified vulnerabilities.
- Simulated attack scenarios.
- Executive and technical-level reporting.
- Retesting after remediation.
This level is typically suited for high-risk systems, regulated environments, or complex architectures where standard vulnerability assessments are not enough.
Vulnerability Assessment vs Penetration Testing Cost
These two terms are often confused, but pricing reflects real differences.
A vulnerability assessment focuses on identifying and prioritizing weaknesses. It emphasizes coverage.
A penetration test focuses on exploiting weaknesses to understand real impact. It emphasizes depth.
Typical cost comparison:
- Vulnerability assessment: $1,000 to $5,000
- Penetration testing: $5,000 to $30,000+
In most market cases, penetration testing priced under $4,000 indicates an automated scan rather than a true manual pentest, though exceptions may exist depending on scope and provider.
Common Pricing Models Explained
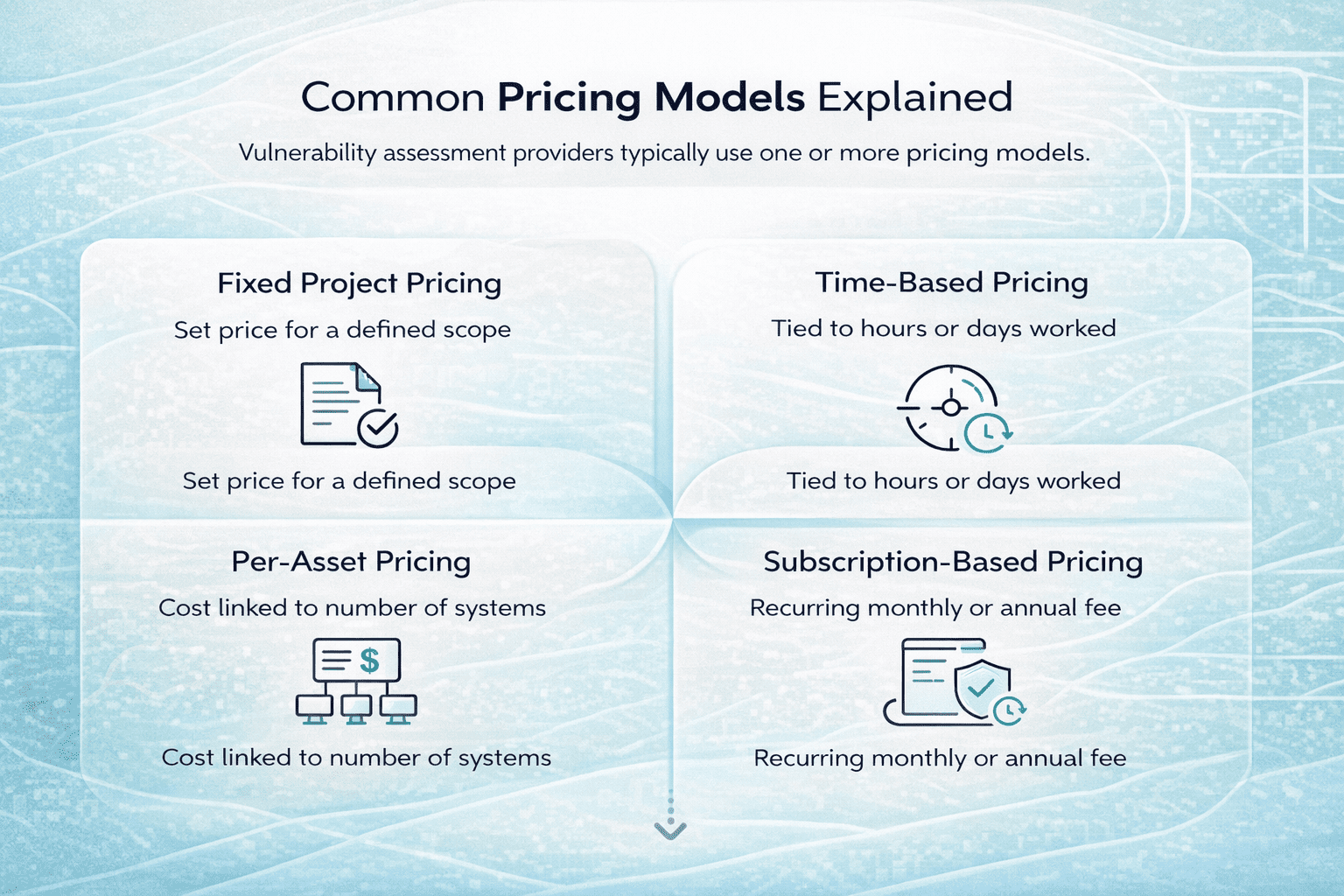
Vulnerability assessment providers typically use one or more pricing models.
Fixed Project Pricing
Fixed Project Pricing is built around a clearly defined scope and a single agreed price. This model works best when everyone knows exactly what needs to be tested, which systems are in scope, and what the final deliverables should look like. From a budgeting perspective, it is straightforward and predictable, which is why many companies prefer it for compliance-driven or one-off assessments. The main limitation is flexibility. If the scope changes mid-project, adjustments usually mean renegotiation.
Time-Based Pricing
With Time-Based Pricing, the cost is tied to the number of hours or days the assessment team spends on the work. This approach offers more flexibility and is often used when the scope is not fully defined at the start or when the engagement is more exploratory. It allows teams to dig deeper as new findings appear, but it can be harder to predict the final cost. For complex environments or evolving systems, this model can make sense as long as expectations and limits are clearly discussed upfront.
Per-Asset Pricing
Per-Asset Pricing links the cost directly to the number of systems being tested, such as endpoints, servers, or applications. This model scales naturally as infrastructure grows and can be easier to understand for organizations with large but consistent environments. However, it does not always reflect complexity. Two assets may require very different levels of effort, so this model works best when assets are relatively similar in structure and risk profile.
Subscription-Based Pricing
Subscription-Based Pricing focuses on ongoing vulnerability scanning for a recurring monthly or annual fee. This model is designed for continuous visibility rather than one-time insight. It works well for organizations that want regular updates as their systems change over time. In practice, subscriptions are often paired with periodic manual reviews or deeper assessments to validate findings and provide context that automated scanning alone cannot deliver.
Choosing the right model depends on how stable your environment is and how often you need insight.
Why Cheap Vulnerability Assessments Often Disappoint
Low pricing is not always bad, but it often comes with trade-offs.
Common issues include:
- High false positives.
- No validation of findings.
- Generic reports with little context.
- No support for remediation.
- No retesting.
A long report does not equal better security. Clarity matters more than volume.
How to Get Better Value From Your Assessment Budget
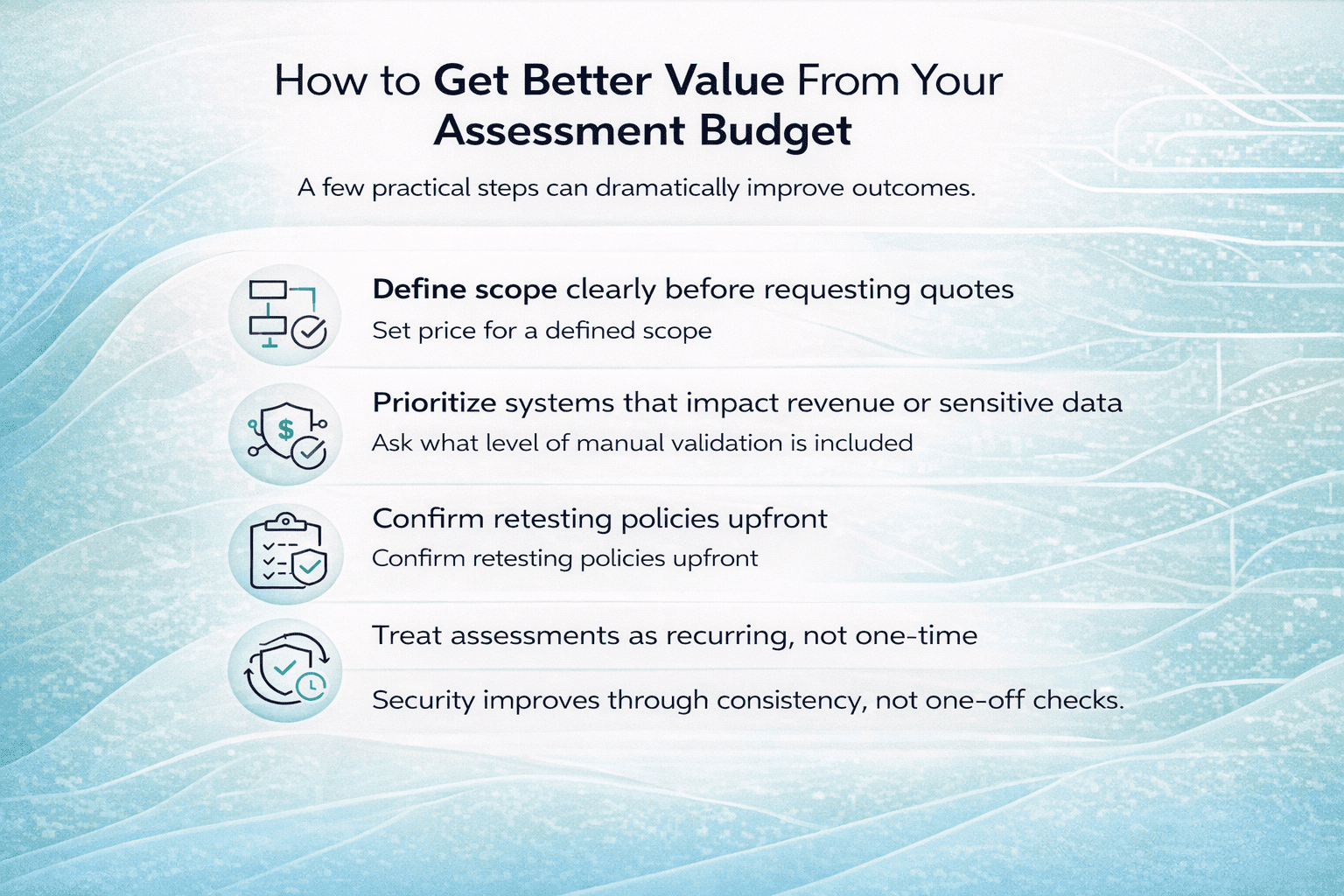
A few practical steps can dramatically improve outcomes.
- Define scope clearly before requesting quotes.
- Prioritize systems that impact revenue or sensitive data.
- Ask what level of manual validation is included.
- Confirm retesting policies upfront.
- Treat assessments as recurring, not one-time.
Security improves through consistency, not one-off checks.
The Real ROI of Vulnerability Assessments
It is easy to view assessments as an expense. It is more accurate to view them as risk reduction.
A modest assessment that prevents one serious incident can justify years of testing costs. Beyond breach prevention, assessments also support compliance efforts, improve audit readiness, reduce operational surprises, and strengthen security culture.
The value is not in the report. It is in what gets fixed afterward.
Réflexions finales
Vulnerability assessment cost is not about finding the cheapest option. It is about understanding what level of visibility your business actually needs and paying accordingly.
For most organizations, the right approach sits between extremes. Enough depth to uncover meaningful risk, without unnecessary complexity or overspending.
When done properly, vulnerability assessments stop being a checkbox and start becoming a practical decision-making tool. And that is where their real value lies.
FAQ
- How much does a typical vulnerability assessment cost?
The cost really hinges on what you’re testing and how thorough the assessment needs to be. For a single web application, vulnerability assessments typically fall between $1,000 and $5,000, depending on the level of access, complexity, and detail involved. In larger environments or cases involving strict compliance standards, total costs can climb well past $30,000. Ultimately, it’s the scope, depth, and the team’s expertise that shape the final number.
- Why do prices vary so much between vendors?
Not all assessments are created equal. Some teams just run automated scans and call it a day. Others dig in manually, validate findings, and simulate real-world attacks. You’re not just paying for tools – you’re paying for expertise, time, and judgment. That’s why a cheaper quote isn’t always better.
- Is it better to go with a fixed price or hourly rate?
If you have a clear scope and want predictable budgeting, fixed pricing is usually safer. But if the project is more open-ended or exploratory, hourly or daily rates can give you more flexibility. Just make sure you set boundaries so the bill doesn’t get out of hand.
- Do I need to test everything at once?
Not necessarily. It’s often smarter to start with your most critical assets – the things that hold sensitive data or power key operations. Then expand testing over time. A phased approach keeps budgets manageable while still reducing risk.
- How often should vulnerability assessments be done?
At a minimum, once a year is a common benchmark. But if you’re making frequent changes, adding new systems, or have regulatory pressure, quarterly or even continuous testing (with subscriptions) might make more sense.
- What’s usually included in the price?
Most assessments include scoping, testing, validation, a report with findings, and a review call to walk through the results. Some teams also help with remediation guidance. Be sure to ask exactly what’s included, don’t assume.


