Predictive analytics sounds expensive for a reason, and sometimes it is. But the real cost isn’t just about machine learning models or fancy dashboards. It’s about the work behind the scenes: data quality, integration, ongoing tuning, and the people needed to keep predictions useful as the business changes.
Many companies budget for “analytics” as if it were a one-time build. In practice, predictive analytics is an ongoing capability, not a static feature. Costs vary widely depending on how ambitious the goals are, how messy the data is, and how quickly insights need to turn into action.
This article breaks down what predictive analytics actually costs, why pricing ranges are so broad, and where teams most often misjudge the real investment.
What Predictive Analytics Actually Includes
Before talking numbers, it helps to clarify what predictive analytics really means in practice. The term gets used loosely, which is one reason budgets often drift later.
At its core, predictive analytics uses historical and current data to estimate what is likely to happen next, such as customer churn, demand, fraud risk, or equipment failure. Building that capability usually involves more than a single model.
A typical predictive analytics setup includes:
- Data ingestion from multiple sources
- Data cleaning and preparation
- Feature engineering and exploration
- Model selection, training, and validation
- Deployment into real systems
- Monitoring and retraining as data changes
As a rough guide, focused predictive projects often start around $20,000 to $40,000. Broader systems with multiple use cases and deeper integrations usually fall in the $40,000 to $75,000 range. Advanced, real-time platforms can push well beyond $100,000.
Some teams stop early and keep things simple. Others build predictive systems that become part of daily decision-making. Costs grow with scope, speed, and how much the business relies on the predictions.
The Biggest Cost Driver: Data, Not Models
One of the most common mistakes teams make is assuming predictive analytics cost is driven mainly by machine learning complexity. In reality, data work usually consumes the largest share of time and budget, especially early on.
Data Collection and Integration
Most companies do not have clean, unified data sitting in one place. Predictive analytics often pulls from CRMs, ERPs, product databases, marketing platforms, financial systems, and sometimes third-party sources. Connecting these systems takes time and coordination.
If APIs are well documented and stable, integration stays manageable. When data lives in legacy tools, spreadsheets, or poorly structured databases, costs rise quickly. Each additional source adds testing, error handling, and long-term maintenance.
Typical Cost Range
$5,000 to $25,000 depending on the number of sources and integration complexity.
Data Cleaning and Preparation
Raw data is rarely usable as-is. Missing values, inconsistent formats, duplicates, and outdated records are common. In many projects, data preparation alone accounts for half or more of the total effort.
This work directly affects prediction quality. Skipping it often leads to models that look convincing in demos but fail once real decisions depend on them. Underbudgeting here is one of the fastest ways to derail a predictive analytics project.
Typical Cost Range
$5,000 to $30,000 depending on data quality and volume.
Modeling Costs: From Simple Forecasts to Advanced AI
Once data is usable, modeling becomes the focus. Costs here vary widely based on prediction type, accuracy expectations, and how often models need to run or update.
Basic Predictive Models
For many business use cases, simpler models work well. Linear regression, logistic regression, decision trees, and basic time-series models can deliver reliable forecasts when the problem is clearly defined.
These models are faster to build, easier to explain to stakeholders, and cheaper to maintain. For teams new to predictive analytics, they are often the most cost-effective starting point.
Typical Cost Range
$5,000 to $15,000 for development and validation.
Advanced Machine Learning and Deep Learning
Costs increase when predictions require more complex approaches. Common examples include image or video analysis, natural language processing, or highly granular real-time predictions.
Advanced models require experienced data scientists, longer training cycles, and more computing resources. They also demand stronger monitoring, since performance can degrade faster as data patterns change.
Higher complexity does not automatically mean better outcomes. Many teams overspend here before confirming that simpler models cannot meet the business need.
Typical Cost Range
$15,000 to $50,000 or more depending on model type and scale.
Infrastructure and Tooling Costs
Predictive analytics does not run in isolation. It relies on infrastructure for data storage, processing, and model execution, all of which affect ongoing costs.
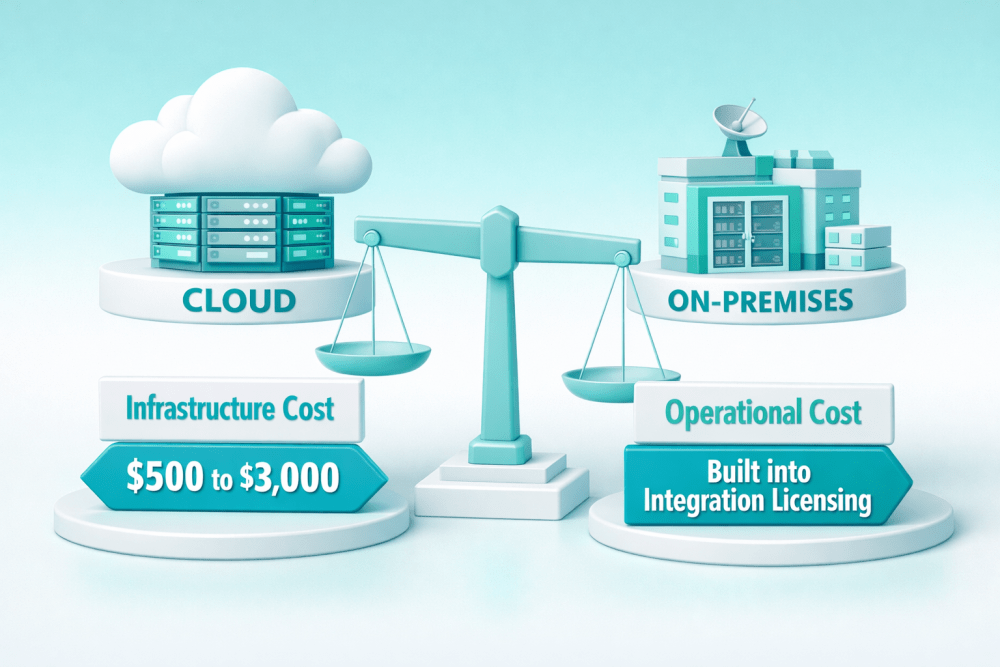
Cloud Versus On-Premise
Cloud platforms make it easier to start quickly and scale as usage grows. Costs are usually usage-based, which suits experimentation but can increase once models move into production.
On-premise setups require higher upfront investment but offer tighter control. They are typically chosen for compliance-heavy environments or large, predictable workloads.
Typical Cost Range
$200 to $5,000+ per month depending on scale and usage.
Compute and Storage
Training and running models can be compute-intensive, especially when working with large datasets or frequent predictions. GPU usage, storage growth, and high-throughput pipelines all contribute to monthly infrastructure bills.
Teams often underestimate these costs by focusing on development only, not steady-state operation.
Typical Cost Range
$300 to $3,000+ per month for active production systems.
Ongoing Costs: The Part Most Budgets Miss
A major misconception about predictive analytics cost is treating it as a one-time build. In practice, ongoing costs often exceed the initial development budget over time.
Model Maintenance and Retraining
Data changes, customer behavior shifts, and markets evolve. Models that are not retrained gradually lose accuracy and relevance.
Ongoing maintenance includes retraining models, updating features, adjusting thresholds, and validating results against new data. This work is continuous, not occasional.
Typical Cost Range
$500 to $3,000 per month depending on model complexity and update frequency.
Monitoring and Support
Production systems require monitoring for failures, anomalies, and performance drops. Someone needs to own alerts, investigate issues, and communicate when predictions behave unexpectedly.
Support may be handled internally or by an external partner, but it needs to be planned and budgeted.
Typical Cost Range
$500 to $2,000 per month depending on SLA and response expectations.
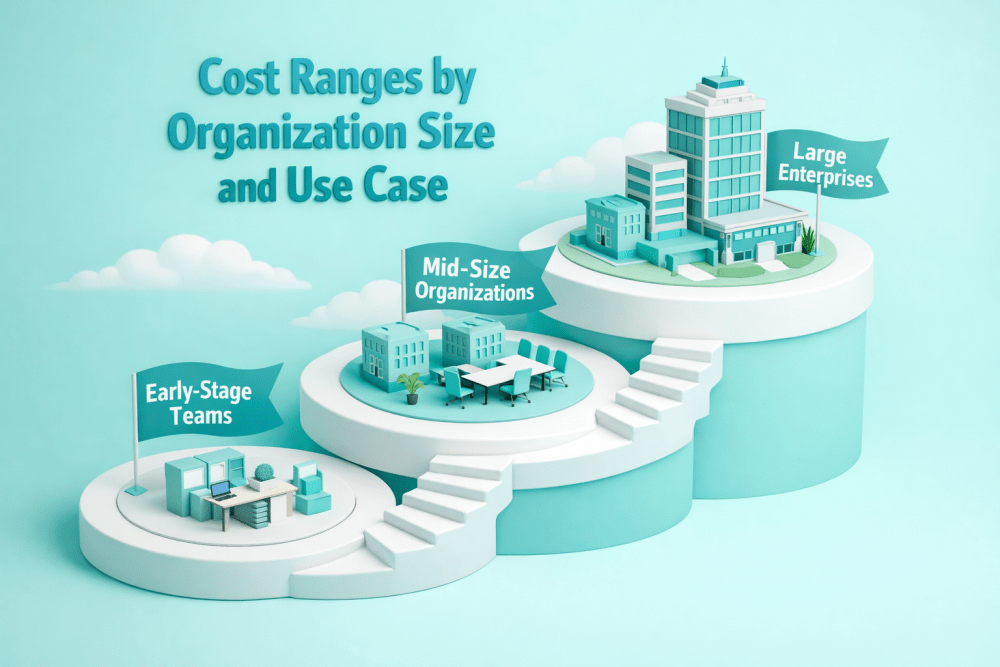
Cost by Business Size
Predictive analytics costs scale less with company size and more with data complexity, decision speed, and operational risk. Still, certain spending patterns tend to repeat across different stages of growth.
Startups and Small Businesses
Smaller companies benefit most from narrow, high-impact use cases such as churn prediction, basic demand forecasting, or lead scoring. Overbuilding predictive analytics early often slows teams down and burns budget without clear returns.
Most small teams rely on limited data sources, simpler models, and cloud-based infrastructure, which helps keep costs predictable.
Typical Cost Range
- $20,000 to $40,000 for initial development
- $200 to $1,000 per month for ongoing operation
Mid-Sized Companies
Mid-sized organizations face rising data volume and system complexity, but predictive analytics also starts delivering clearer operational value. Common use cases include multi-channel forecasting, pricing optimization, and customer segmentation across departments.
Modular builds and phased rollouts help control spend while expanding capability over time. This stage often benefits from a mix of internal ownership and external expertise.
Typical Cost Range
- $40,000 to $75,000 for initial development
- $1,000 to $5,000 per month for ongoing operation
Enterprises
Enterprise environments demand higher investment due to scale, governance requirements, and compliance obligations. Predictive analytics often supports real-time decisions, large user bases, and mission-critical processes.
Costs are higher, but predictive systems typically become a core strategic capability rather than a standalone project.
Typical Cost Range
- $75,000 to $150,000+ for initial development
- $5,000 to $25,000+ per month for ongoing operation

How We Turn Predictive Analytics Into a Practical Advantage at A-listware
At A-listware, we help teams build predictive analytics that actually fits how their business works. With 25+ years of experience in software development and consulting, we know that successful analytics is not about chasing complex models, but about building systems that are reliable, understandable, and useful over time.
We assemble dedicated analytics and engineering teams in as little as 2 to 4 weeks, drawing from a vetted pool of over 100,000 specialists. Our teams integrate directly into your workflows, whether you need a focused predictive model to prove value or a scalable analytics foundation that supports multiple use cases across the organization.
We work as an extension of your team, handling data analytics, machine learning, infrastructure, and ongoing support with clear communication and stable delivery. Companies like Arduino, Qualcomm, Kingspan, and NavBlue choose us because we reduce risk, keep costs under control, and build predictive systems that continue delivering value long after launch.
How To Budget Predictive Analytics More Accurately
Teams that get consistent value from predictive analytics treat it as an evolving capability, not a one-off project. Budgeting works best when it reflects how these systems actually grow and mature over time.
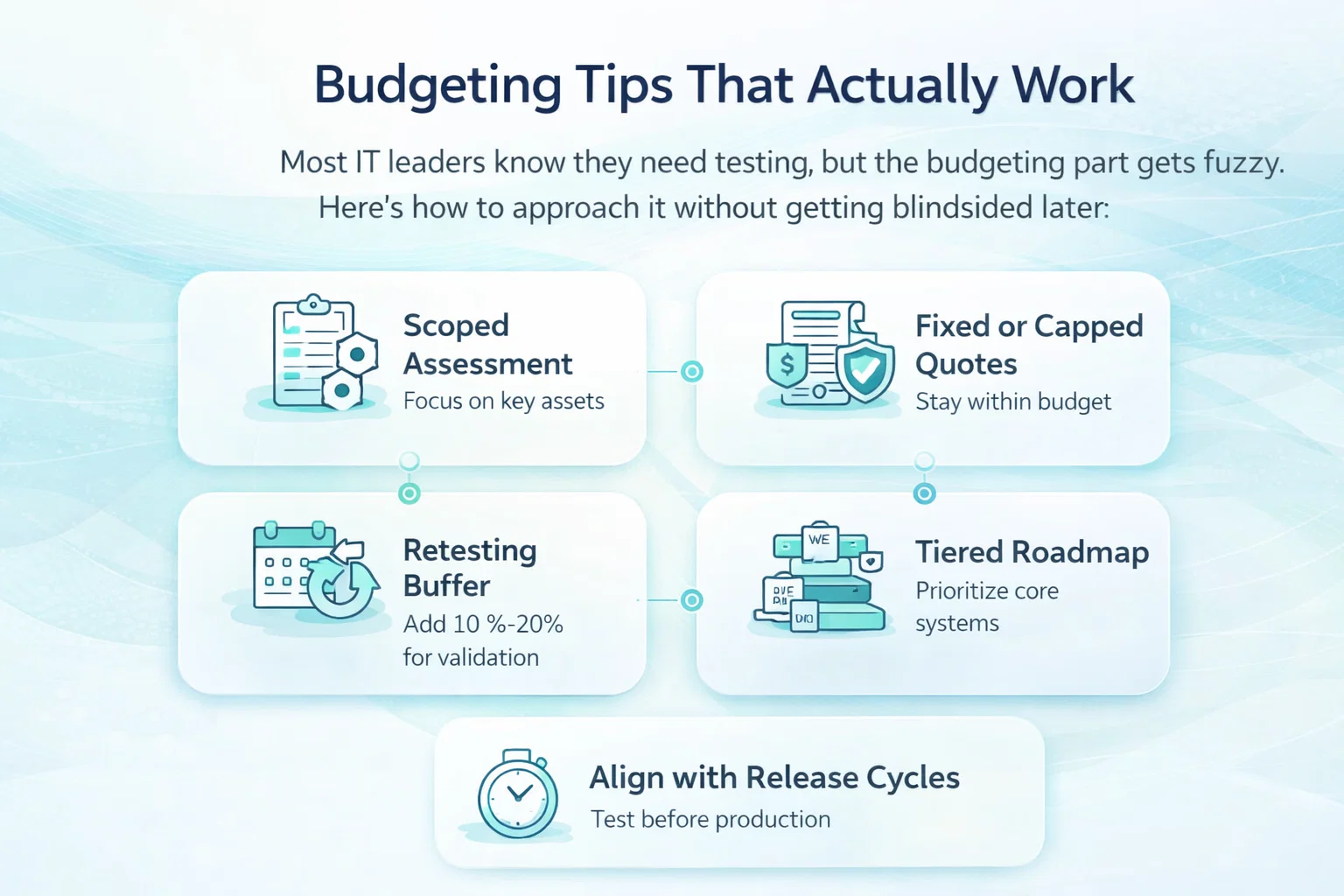
- Start With Business Questions, Not Tools. Define the decisions you want to improve before choosing platforms or models. A clear question like “which customers are likely to churn” leads to tighter scope and more realistic cost estimates than starting with a specific technology.
- Prove Value With Simpler Models First. In many cases, basic predictive models deliver most of the value at a fraction of the cost. Starting simple helps teams validate assumptions, build trust in the outputs, and avoid over-investing before the use case is proven.
- Budget For Data Work And Ongoing Maintenance. Data integration, cleaning, and monitoring are not one-time tasks. Set aside budget for continuous data quality work, model retraining, and system updates, even after the initial build is complete.
- Expect Iteration, Not Instant Precision. Predictive analytics improves through feedback and adjustment. Early models rarely get everything right. Budget time and resources for refinement instead of assuming accuracy will be perfect from day one.
- Measure Success By Decisions Improved. Focus on whether predictions lead to better actions, not just better metrics. If teams make faster, more confident decisions or avoid costly mistakes, the investment is doing its job.
Common Mistakes That Inflate Predictive Analytics Costs
Even well-funded teams overspend on predictive analytics, often without realizing why. The issues are rarely technical failures. More often, they come from planning and expectation gaps early in the process.
Treating Predictive Analytics as a One-Off Project
One of the most expensive assumptions is thinking predictive analytics ends at deployment. Models need retraining, data pipelines need maintenance, and predictions need regular validation. Teams that budget only for initial development usually face rushed fixes later, which cost more than steady upkeep.
Starting With Technology Instead of a Use Case
Choosing tools, platforms, or AI techniques before defining the business problem often leads to unnecessary complexity. This usually results in overbuilt systems that are expensive to maintain and difficult for stakeholders to trust or use.
Underestimating Data Readiness
Many projects assume data is cleaner and more complete than it actually is. When data quality issues surface mid-project, timelines slip and costs rise. A realistic data audit early on is far cheaper than emergency cleanup later.
Overengineering Accuracy Too Early
Pushing for near-perfect predictions from day one is a common budget killer. Early models are meant to guide decisions, not eliminate uncertainty entirely. Teams that allow room for iteration usually reach better outcomes with lower total spend.
Ignoring Adoption and Change Management
Predictions that are not used do not create value. When teams skip training, documentation, or workflow integration, analytics systems sit unused while costs continue. Budgeting for adoption is just as important as budgeting for development.
Final Thoughts
Predictive analytics cost is rarely about the model alone. It reflects the condition of your data, the speed at which insights are expected, and how much risk the business is willing to place on automated predictions. Teams that underestimate these factors often find themselves paying more later, either through rushed fixes or systems that never quite earn trust.
When budgeting reflects that reality, predictive analytics stops feeling like a gamble. It becomes a capability that improves over time, supports better decisions, and justifies its cost through consistent, measurable impact rather than promises on a slide deck.
Frequently Asked Questions
- How much does predictive analytics typically cost?
Predictive analytics projects usually start around $20,000 to $40,000 for focused use cases with limited data sources. More advanced systems with multiple integrations or real-time predictions often fall between $40,000 and $75,000. Enterprise-grade platforms can exceed $100,000, especially when compliance, scale, and ongoing optimization are required.
- Why do predictive analytics costs vary so much?
Costs vary mainly because data quality, system complexity, and business expectations differ widely. A clean dataset and a simple forecasting goal cost far less than real-time predictions built on fragmented or legacy data. Accuracy requirements and operational risk also play a big role.
- Is predictive analytics a one-time cost?
No. Initial development is only part of the investment. Ongoing costs include data maintenance, model retraining, infrastructure usage, monitoring, and support. For many teams, monthly operating costs continue long after the first deployment.
- Can small businesses use predictive analytics without overspending?
Yes, as long as scope is controlled. Small teams benefit most from narrow, high-impact use cases and simpler models. Starting small helps prove value before committing to larger investments.
- Are advanced AI models always worth the extra cost?
Not always. In many cases, simpler statistical or machine learning models deliver reliable results at a lower cost. Advanced models make sense when the problem truly requires them, not just because they sound more impressive.