Zero Trust isn’t just another security buzzword – it’s quickly becoming the standard for how companies protect systems, data, and people. But while the benefits are widely discussed, the cost side often gets blurred. Some think it’s just a VPN upgrade. Others assume it’s a seven-figure security overhaul. The truth sits somewhere in between, shaped by how you approach it and how prepared your IT landscape already is. Let’s walk through what Zero Trust architecture actually costs, what drives those numbers up or down, and where most teams go wrong when budgeting for it.
What Zero Trust Actually Costs and Why Guesswork Backfires
When teams start planning a Zero Trust rollout, one of the first questions that comes up – sometimes quietly – is “how much is this going to cost us?” The honest answer is: it depends, and if someone gives you a flat number without looking at your infrastructure, they’re guessing. The cost of Zero Trust isn’t just about licenses or platforms – it’s about how ready you are to untangle your application sprawl, how mature your access controls are, and whether you treat the project as a patch or a real modernization push.
What makes transparency so important here is that bad assumptions turn into expensive mistakes. Some companies rush in thinking it’s just a matter of switching off VPNs. Others throw money at consultants without a clear inventory or integration plan. Either way, the budget starts burning before the benefits kick in. Clear planning, realistic ranges, and understanding where the time and effort actually go – that’s what separates costly rework from a Zero Trust architecture that scales cleanly and pays off.
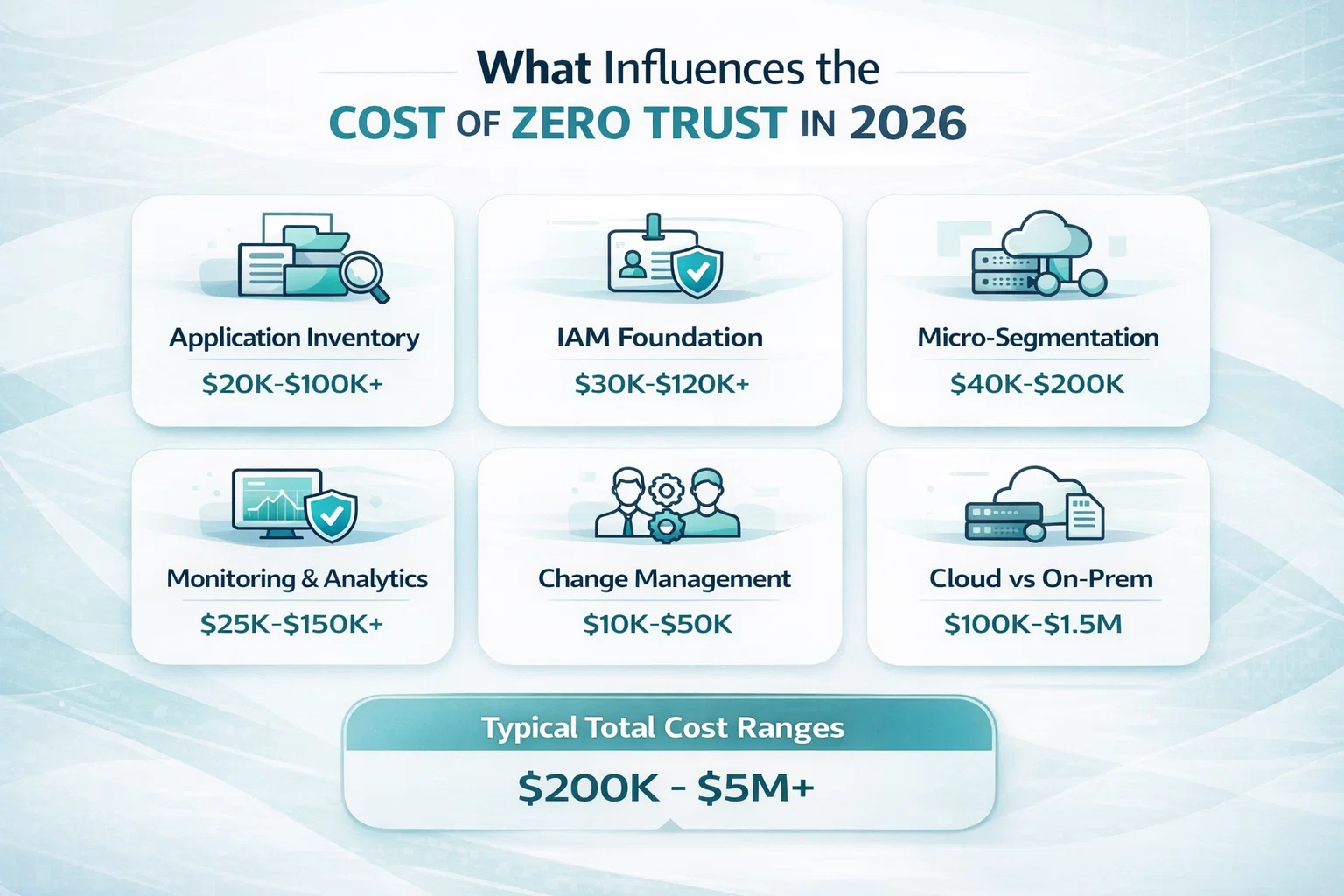
What Influences the Cost of Zero Trust in 2026
Zero Trust isn’t something you buy off the shelf. It’s built around how your systems, teams, and risks actually work, and that’s why costs vary so much – even between companies of the same size.
Some organizations roll it out in phases for under $150,000. Others cross the $2 million mark when legacy systems, siloed ownership, or strict compliance requirements come into play. The difference usually comes down to how much groundwork is already done.
1. Application Inventory: The Hidden Budget Line
One of the most underestimated cost drivers is figuring out what you actually run. For companies without a clean system inventory, this step alone can take weeks – and cost tens of thousands in internal engineering time and external assessment tools.
- Expect $20,000-$100,000+ depending on how complex your application landscape is.
- In highly fragmented environments, costs can spike due to manual mapping, audit gaps, and duplicated tools.
2. IAM Foundation and Policy Design
Zero Trust relies on strong identity and access management (IAM). If you already have centralized IAM and MFA in place, that’s a head start. If not, you’re looking at foundational upgrades.
- Licensing and integration work often ranges from $30,000 to $120,000.
- Complex role-based access models or regulatory-grade identity workflows (e.g. in finance or healthcare) can push it higher.
3. Micro-Segmentation and Network Architecture
Creating secure zones around apps and systems isn’t free. It takes serious planning, configuration time, and sometimes reengineering how services talk to each other.
- For mid-size environments, segmentation projects often fall in the $40,000-$200,000 range.
- Heavily integrated or legacy-heavy networks may require custom tooling and multi-phase rollouts.
4. Real-Time Monitoring and Analytics
Zero Trust without visibility is just wishful thinking. Real-time monitoring, behavioral analysis, and anomaly detection are essential – but also pricey depending on scope.
- Most companies spend between $25,000-$150,000 on tools, setup, and tuning in the first year.
- Costs go up fast if you want full-stack observability across hybrid environments.
5. Change Management, Training, and Internal Alignment
Even with perfect tooling, Zero Trust fails when teams don’t buy in. Training users, updating policies, and managing the transition is where a lot of “soft costs” show up.
- Budget at least $10,000-$50,000 for proper change management.
- Enterprises with global teams or high turnover should double that estimate.
6. Cloud vs On-Prem: Deployment Context Matters
The deployment model also shifts the price tag. Cloud-native companies often move faster and spend less upfront – around $100K-$250K. Hybrid or on-prem-heavy organizations typically face higher integration and operations costs – $300K-$1.5M depending on scale.
7. Typical Total Cost Ranges in 2026
Here’s how Zero Trust investment stacks up based on company size and complexity:
| Company Type | Estimated 2026 Cost |
| Small Business (Cloud-native, 100-500 employees) | $180,000-$450,000 |
| Mid-Market (Hybrid, 500-2,500 employees) | $450,000-$1.2M |
| Large Enterprise (Multi-cloud + Legacy) | $3.5M-$5M+ |
There’s no flat price tag. What really drives cost is how ready you are to clean up what’s already in place. Skipping that work usually backfires – and fast.
A-listware in Action: Practical Zero Trust, Step by Step
За адресою Програмне забезпечення списку А, we don’t just drop in tools and leave. Our approach to Zero Trust is shaped around real-world systems, existing workflows, and the people who use them. Whether you’re modernizing legacy infrastructure or starting cloud-first, we work alongside your team to design secure architecture that fits how your business actually runs.
Zero Trust only works when it reflects how your team operates. That’s why we focus on structured discovery, realistic access policies, and hands-on collaboration. We stay close through each stage – so decisions stay practical, and implementation stays on track.
We share our process and insights openly. If you’d like to see how the team thinks or what’s currently in progress, follow us on LinkedIn or Facebook.
Why “Just Replacing VPNs” Ends Up Costing More
Swapping a legacy VPN for a Zero Trust tool might seem like a clean upgrade. But treating it as a one-to-one replacement usually backfires. It preserves outdated access patterns, adds complexity, and does nothing to clean up what’s under the surface. Costs pile up fast – especially when no one’s asking which systems still matter or who’s actually using them.
Instead of modernizing, you end up securing abandoned tools, renewing unused licenses, and writing policies around guesswork. It’s a shortcut that looks cheaper on paper, but drags technical debt forward. The better approach is slower at first: fix what’s broken, drop what’s obsolete, and then secure what’s left. That’s where Zero Trust starts delivering real value.
Where Zero Trust Pays for Itself (and Then Some)
Zero Trust isn’t cheap to roll out – but it starts paying off faster than most expect. The real value shows up not just in better security, but in everything it helps you clean up, retire, or automate. And that impact is easy to measure: smaller bills, tighter audits, and fewer wasted hours. Here’s where the value tends to land hardest:
- License optimization: On average, teams cut software licensing costs by 20-40% simply by retiring unused or duplicate systems during inventory.
- Infrastructure savings: Consolidation and reduced load often translate to lower compute, storage, and network costs – especially in hybrid environments.
- Reduced breach exposure: Companies with mature Zero Trust implementations save up to $1.76 million per data breach (based on 2024-2025 industry data).
- Fewer security tools to manage: With tighter policies and better visibility, many orgs retire redundant tools and shrink their security stack.
- Smaller attack surface: Micro-segmentation, least-privilege access, and continuous verification cut down lateral movement risk – and the cleanup costs that follow a breach.
- Faster response times: Teams that actually know what assets they own and how they’re connected resolve incidents faster and with more confidence.
- Simpler audits and compliance checks: Granular logging and policy-based access reduce prep time for external audits and internal reviews.
- Less manual work: With automation and unified controls, fewer things fall through the cracks, and engineers spend less time putting out fires.
It’s not just about building better security – it’s about getting rid of expensive noise and replacing it with something that actually scales. That’s where the return really kicks in.
How Long Zero Trust Really Takes and When the Costs Hit
Most Zero Trust rollouts take 12 to 18 months, but the real story is less about the total timeline and more about how the work breaks down. The early phase – getting your inventory in order, mapping data flows, and setting up IAM – tends to be the most resource-heavy. That’s where a big chunk of the initial cost lands. You’re not just configuring tools – you’re fixing long-ignored access patterns and dependencies that were never properly documented.
Once the foundation’s in place, costs shift. Micro-segmentation, policy enforcement, and monitoring tools come next, but they usually follow a steadier pace and more predictable spend. Teams that phase implementation smartly often see early wins (like license savings or risk reductions) kick in by month 6-8. By the time you hit month 12, Zero Trust stops looking like a security project and starts acting like an operational upgrade. The value builds quietly – and sticks.
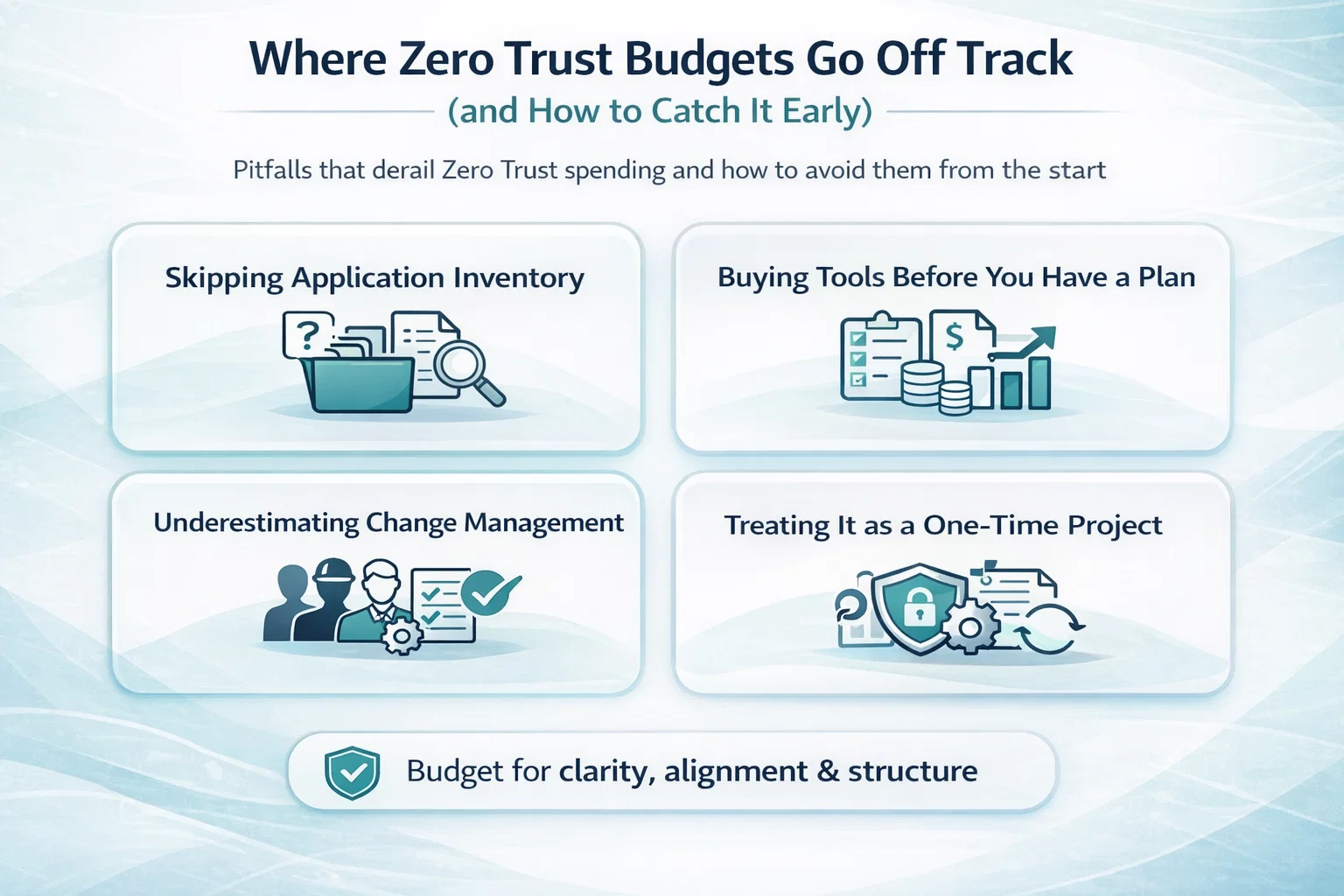
Where Zero Trust Budgets Go Off Track (and How to Catch It Early)
Zero Trust can absolutely deliver long-term savings – but not if you burn half your budget on the wrong things. A lot of teams fall into the same traps: rushing rollout, buying too many tools, or ignoring internal readiness. Below are a few of the most common reasons costs spiral, along with how to sidestep them before it’s too late.
Skipping Application Inventory
Going straight to tech deployment without understanding what you actually own is like renovating a building without checking what’s behind the walls. You end up securing dead systems, duplicating controls, and carrying forward technical debt. This step isn’t glamorous, but skipping it almost always leads to budget creep and missed opportunities for consolidation.
Buying Tools Before You Have a Plan
It’s easy to overinvest in platforms and licenses before the architecture is mapped out. Some vendors promise “out-of-the-box Zero Trust,” but that usually translates into overlapping features or shelfware later. A phased strategy – anchored in actual business needs – almost always leads to better spend discipline.
Underestimating Change Management
Even the best Zero Trust plan will stall if your teams don’t know how to work within it. Failing to budget for user training, policy rollout, or cross-team coordination adds hidden costs fast. Misalignment here leads to workarounds, shadow IT, and resistance that can quietly wreck timelines.
Treating It as a One-Time Project
Zero Trust isn’t a set-it-and-forget-it system. Ongoing tuning, audits, and policy adjustments are part of the deal. If you treat it like a one-and-done rollout, the system slowly drifts out of sync with real usage – and the costs come back as incident response, rework, and compliance risks.
The most successful teams budget not just for tech, but for clarity – inventory, alignment, and structure. That’s where overspending turns into smart investment.
Висновок
Zero Trust isn’t a cheap checkbox. It’s a strategic rebuild – and like most rebuilds, it either exposes old problems or quietly covers them up. The real cost isn’t in the tools you buy, but in the decisions you make along the way: what you keep, what you cut, and how well you understand your own infrastructure. Companies that approach it as a security upgrade tend to overspend. The ones that treat it as a cleanup and modernization effort usually get more value for less.
Done right, Zero Trust pays off not just in fewer breaches or cleaner audits, but in faster response times, simpler operations, and clearer visibility across the board. That payoff doesn’t come from throwing money at new platforms – it comes from knowing exactly what you’re securing and why. Everything else builds on that.
ПОШИРЕНІ ЗАПИТАННЯ
- How much does Zero Trust cost in 2026?
It depends on how complex your environment is and how ready you are. A small cloud-native company might spend under $150K. A large enterprise with legacy sprawl could hit $2 million or more, especially if compliance or segmentation work is intensive.
- Is there a way to keep costs down without cutting corners?
Yes. The biggest savings come from rationalizing your app portfolio early. Clean up what you don’t need, avoid buying overlapping tools, and roll out in phases. Don’t skip the groundwork – it’s where most of the value hides.
- Can we just replace our VPN and call it Zero Trust?
You can, but it won’t do much. You’ll end up layering new tech over the same outdated structure and paying for systems and access you don’t actually need. Zero Trust works when it changes how your environment is structured – not just how it’s accessed.
- What’s the typical timeline for implementation?
Most companies take 12-18 months from first assessment to full deployment. The timeline depends on how much cleanup and internal alignment is needed. You’ll likely see meaningful benefits by month six if it’s rolled out strategically.
- Does Zero Trust work for hybrid or on-prem environments?
It does, but the cost and complexity go up. Legacy systems and fragmented networks take more work to segment, monitor, and control. Still, it’s doable – and worth it long-term, especially if you approach it as part of a broader modernization push.


